IAM Challenges for Hospitals and Healthcare Providers
To guarantee the highest possible standard of medical care, healthcare institutions rely on cutting-edge technology, including the latest imaging techniques and digital online systems for storing patient data. Unfortunately, the use of such technologies in hospitals bears not only benefits, but also security risks: Health data stored and processed in hospital networks presents an especially tempting target for hackers and cybercriminals.
As a result, attacks on healthcare organizations are very much on the rise. In fact, 34% of healthcare organizations were reportedly hit by a ransomware attack in 2020. In one such case that occurred at an Indianapolis-based health system earlier this year, patient data was exfiltrated and leaked. The affected hospital was forced to shut down its IT system and all patient traffic had to be diverted to other healthcare facilities for several days. In a particularly tragic example, a patient who had to be turned away by a German hospital that had suffered a cyberattack is considered the world’s first death caused by ransomware.
Protecting Private Health Information Under HIPAA
To guarantee that hospitals and other healthcare providers can continue to provide sufficient care to their patients and keep private health information both confidential and safe, all healthcare providers in the US are required to comply with HIPAA, the Healthcare Insurance Portability and Accountability Act of 1996.
HIPAA stipulates that all organizations in the healthcare sector must implement strict privacy and security measures to safeguard private health information of patients. Considering the complex organizational structure at most healthcare facilities, maintaining control of who has access to patient information can put a huge strain on IT staff, who have to manage hundreds of user accounts across numerous medical departments as well as administrative and custodial staff.
Finding ways to standardize and automate processes is therefore key to achieving HIPAA compliance and protecting private health information against cyberattacks.
Identity & Access Management Solutions Compared
Our white paper will help you navigate the IAM market, familiarize you with available products and explain key questions to ask yourself when evaluating IAM solutions.
Tailored to Your Needs: Access Management With tenfold
tenfold allows you to automate routine management tasks quickly and easily. It uses role-based access control to adjust user rights automatically when a person switches departments or leaves your organization entirely.
With its many plugins and very own Generic Connector, tenfold serves as a central platform for user and access management across systems like Active Directory, file servers, the cloud and other external systems like SAP ERP.
IT Security & Compliance
In tenfold, access rights are always assigned in accordance with IT security best practices such as the principle of least privilege, which is one of the requirements of HIPAA. The removal of excess privileges closes dangerous security holes and significantly reduces the risk and scope of cyberattacks.
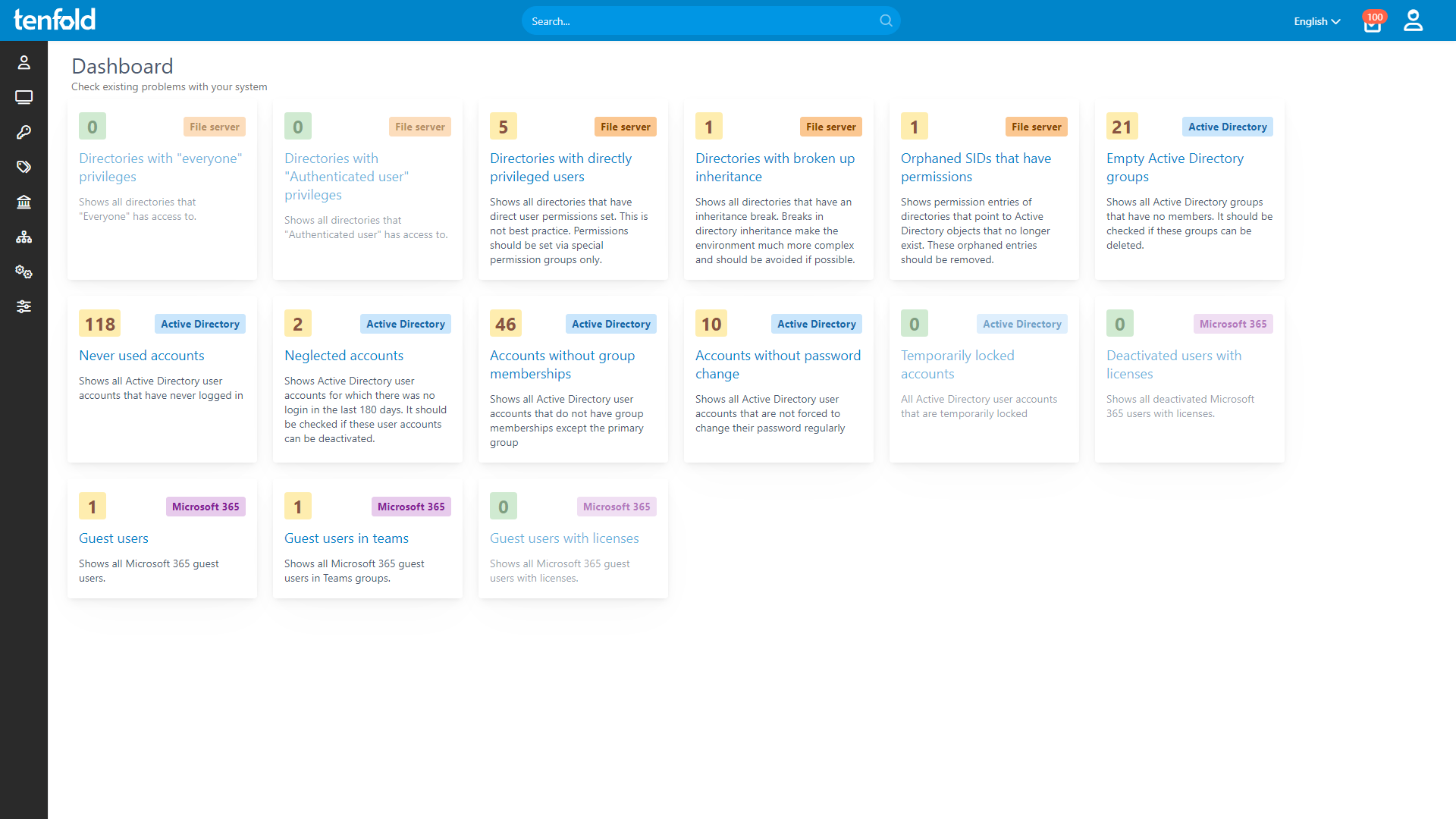
tenfold automatically logs changes and uses approval workflows to track who has access to what resources and who approved said access. It also employs user access reviews to ensure privileges are withdrawn as soon as they are no longer needed and further comes with an excellent reporting tool, allowing you to view access histories in your healthcare institution with just one click.
See tenfold in Action With Our Feature Video
Schedule a Live Demo With One of Our Experts
Put tenfold to the Test With Our Free Trial!