IAM Challenges for Retailers, Distributors & Services
In today’s landscape, businesses in retail, services and distribution handle more data than ever before: customer, payment and supplier data, all vulnerable to security breaches. As staff turnover rates fluctuate, ensuring that only authorized individuals can access sensitive data is essential. Automated access governance allows your org to meet these challenges head on.
Complying With Data Protection Laws
Efficient access governance not only helps companies comply with GDPR, PCI DSS and other data protection requirements but also reduces risks related to excess privileges. Implementing secure IAM strategies is key to minimizing cyberattacks and data theft, helping businesses avoid the severe consequences of customer data breaches.
IGA Solutions Compared
Dive deep into the advantages and disadvantages of different available solutions for Identity Governance & Administration.
Boost Compliance & Productivity
tenfold‘s IAM platform enhances security and efficiency by automating user access management. Centralized user lifecycle management restricts access for every user to the minimum required, aligned with the principle of least privilege, following cybersecurity best practices.
Here’s how it works: When you set up tenfold, it analyzes existing permissions in your org to help you pick baselines access for different roles. As employees join, change roles or leave, tenfold automatically updates their access across all systems, from Active Directory and file servers to Microsoft 365 and workplace apps.
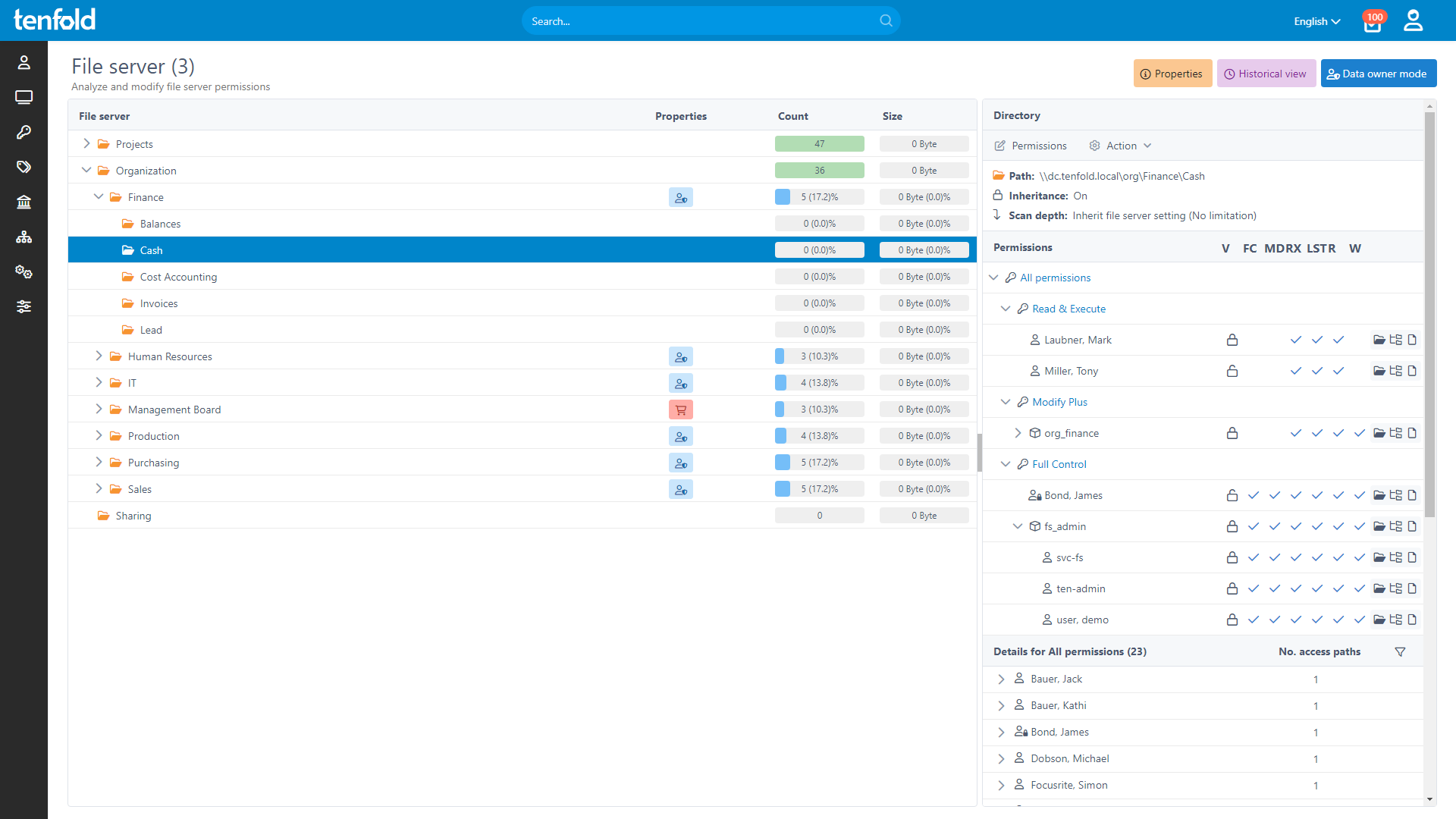
Complete Visibility
Gain full insight into access rights – from individual files to system-level oversight.
Centralized Governance
Govern access in Active Directory, Microsoft 365 and beyond through a single platform.
Fast Implementation
Achieve complete integration faster with our no-code platform and off-the-shelf plugins.
User-Friendly Self-Service & Comprehensive Reporting
Alleviate helpdesk pressure with a self-service portal that allows users to request access to IT resources, reset passwords or obtain permissions independently. Customizable approval workflows allow data owners to manage access for resources they control, eliminating the need for IT intervention.
tenfold logs all permission changes and provides detailed reports showing current and past access rights, ensuring compliance and proof that data has been secured at all times.
See how it works
With full visibility, central auditing and lifecycle automation, tenfold helps you regain control of IT privileges.
Watch our video overview to see it in action.
See tenfold in Action With Our Feature Video
Schedule a Live Demo With One of Our Experts
Put tenfold to the Test With Our Free Trial!