IAM for Water, Energy & Transportation Services
Utility services like water, energy and transportation are essential for a functioning society. Any disruption could have significant social and economic consequences. Events like the Colonial Pipeline hack and resulting gas shortages highlight the importance of securing operational technology (OT) systems, which are increasingly vulnerable to ransomware, malware and hacking. Identity & access management is critical to mitigating these risks by minimizing your attack surface and preventing identity-based attacks.
Critical Infrastructure Cybersecurity
Governments around the world are prioritizing critical infrastructure cybersecurity to combat growing threats. From CISA’s efforts in the US to recent EU legislation like NIS2 and the Cyber Resilience Act (CRA), providers of essential services need to prepare for stricter compliance regulations: comprehensive security frameworks that include the need for access governance.
Cybersecurity Standards for Infrastructure
IGA Solutions Compared
Dive deep into the advantages and disadvantages of different available solutions for Identity Governance & Administration.
Manage Risks and Compliance Challenges with tenfold
To keep up with existing and expanding cybersecurity regulations, infrastructure organizations need to move to a Least Privilege model for IT access. By centralizing access governance with tenfold, essential service providers can limit access rights, prevent identity-based attacks and meet compliance challenges.
Role-based access control enables streamlined access governance by establishing permission roles and bundling together the necessary access for each department and position. Once roles have been set up, automated lifecycle workflows ensure that users receive the correct level of access across systems like Active Directory, Microsoft 365 and various workplace apps. All thanks to tenfold’s simple, no-code integrations.
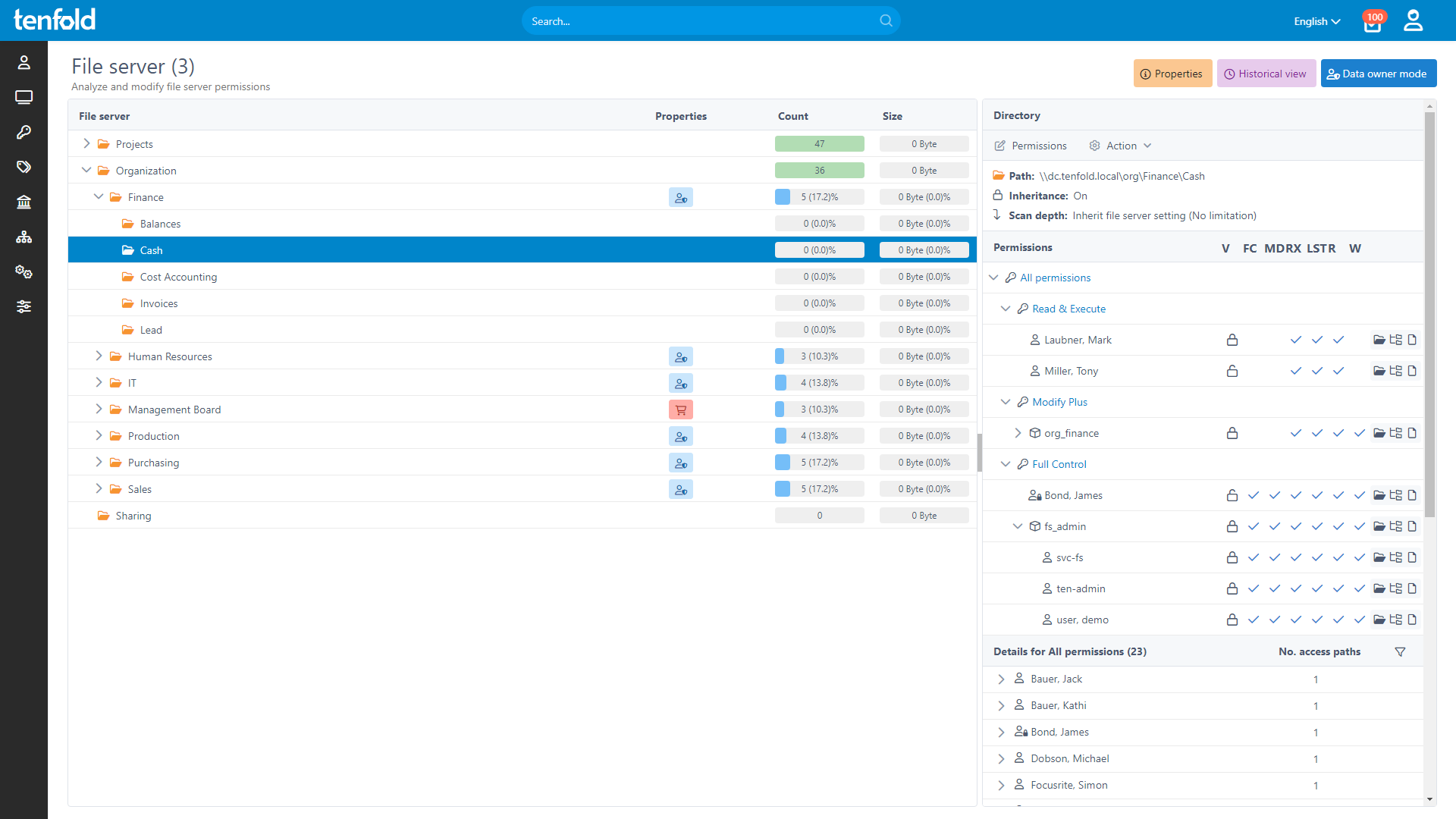
Complete Visibility
Gain full insight into access rights – from individual files to system-level oversight.
Centralized Governance
Govern access in Active Directory, Microsoft 365 and beyond through a single platform.
Fast Implementation
Achieve complete integration faster with our no-code platform and off-the-shelf plugins.
Comprehensive Reporting
tenfold’s self-service interface enables users to request additional permissions if they need them, with requests processed by non-IT users such as team leads or department heads. This allows teams to manage access to their resources independently and reduces the strain on your IT staff.
Our platform logs all changes to access rights and provides centralized permission reporting to ensure a complete audit trail. Generate comprehensive reports detailing privileges for specific users or resources. This allows CTOs, CSOs and CCOs to maintain the highest security standards by providing full visibility into access governance for critical infrastructure sectors.
See how it works
With full visibility, central auditing and lifecycle automation, tenfold helps you regain control of IT privileges.
Watch our video overview to see it in action.
See tenfold in Action With Our Feature Video
Schedule a Live Demo With One of Our Experts
Put tenfold to the Test With Our Free Trial!