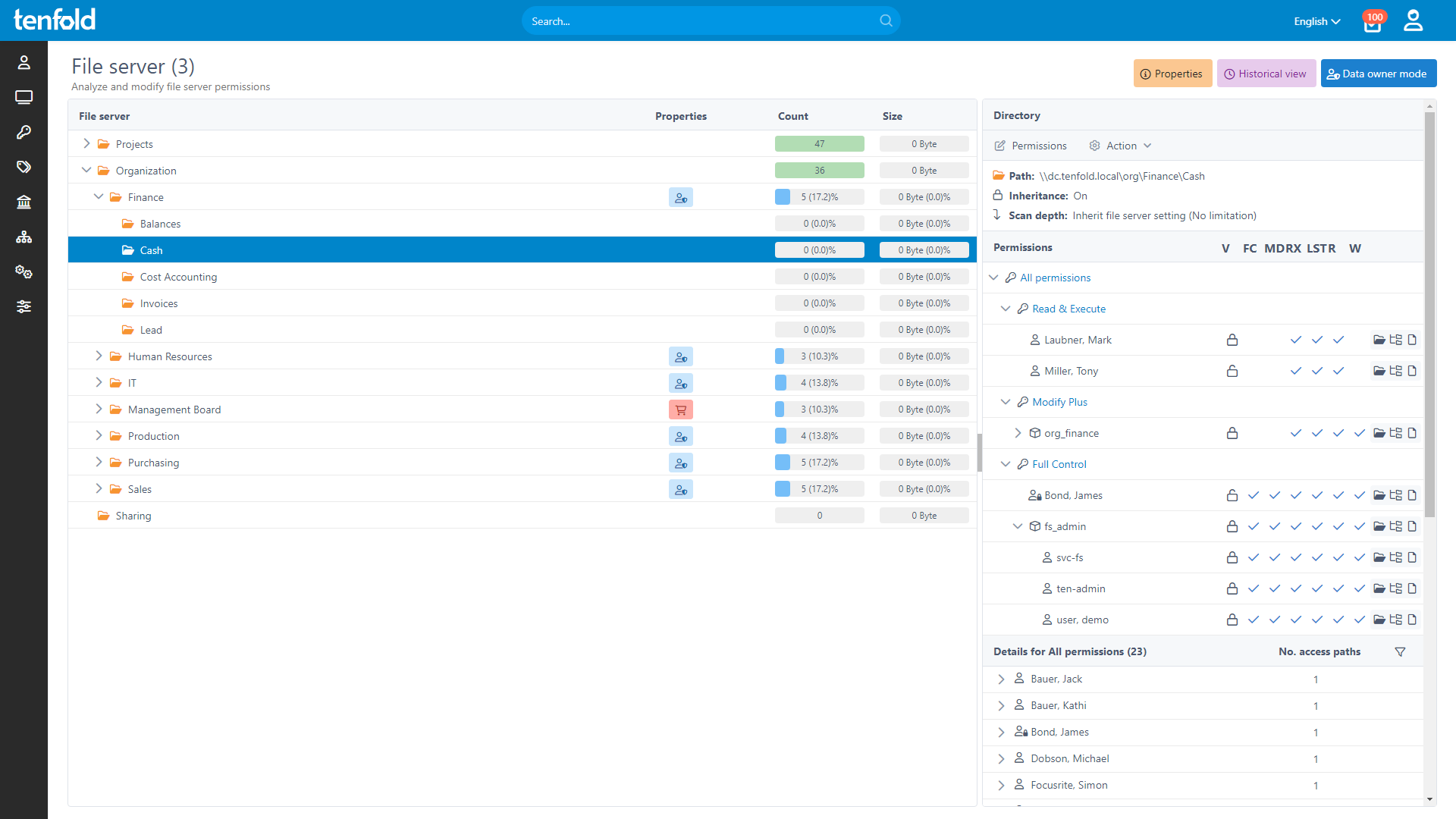
Gain Full Visibility Over Data Access
To secure your organization’s sensitive data, precise control over object-level permissions is essential. tenfold offers a centralized view of who can access what – providing both fine-grained and high level visibility, ensuring full transparency and security for your data.
Visibility Is the Foundation of Security
To safeguard mission-critical data, knowing who can access your files across all systems is essential.
tenfold provides full visibility into permissions at every level, ensuring robust data protection.
See the Full Picture
Get a breakdown of effective permissions
Centralized reporting for all IT systems
Track access to shared files & cloud data
Lock Down Access
Review user & object level permissions
Identify & fix problematic access quickly
Detect and manage external sharing risks
Stay Audit-Ready
Prove compliance with easy reports
Generate complete overviews in seconds
Track changes with historical data
Centralized Permission Reporting
Gain a clear and centralized view of effective permissions, ensuring you always know who has access to which data across your organization.
Comprehensive Change Tracking
tenfold logs all permission changes, role updates and approval workflows, providing a complete audit trail for compliance and security audits.
Identify & Resolve Access Issues
From empty AD groups to broken inheritance, tenfold’s intuitive dashboard highlights common IT misconfigurations and enables you to resolve them with just a few clicks, streamlining operations and improving security.
%
75
Lower IT Workload
%
95
Faster Access Provisioning
%
98
Recommendation Rate on Capterra
%
100
Privilege Creep Reduction
Why Choose tenfold?
tenfold’s quick setup, easy configuration and powerful features make it the ideal choice for anyone looking to securely manage user accounts and IT privileges. Our all-in-one solution combines identity and data access governance into one convenient and user-friendly package.
Download our IAM Comparison
Ready to Try It Yourself?
Cloud Demo Environment
We give you acces to a cloud environment prepopulated with users and a ready-to-go tenfold instance.
Start testing right away
Enjoy our no-code UI and easy configuration
Try our automated workflows in a sandbox environment with prebuilt users & groups
Full access to all of tenfold’s features
7 day trial period
Proof-of-Value Installation
Our consultants help you set up tenfold on your network so you can test it against your own infrastructure.
In-depth test in your own IT environment
Try our no-code plugins and integrations
Turn your demo install into a real deployment (No lost work!)
Full access to all of tenfold’s features
30 day trial period
Frequently Asked Questions
tenfold offers detailed, item- and user-level permission reporting for all connected systems. Admins can access both current and historical data for privileges across different services, as well as generate their own custom reports or export data as PDF or Excel files. By breaking down group memberships and nested structures into effective permissions, tenfold makes it easy to keep track of which systems a particular user can currently and could previously access, as well as which users had access to a particular system.
To help you track all changes made to users’ permissions, the tenfold Auditor shows you a list of days and which adjustments were made on those days. Admins can expand these data points as needed to see which changes were made and who approved them.
tenfold‘s Pathfinder provides a visual representation of users and groups in the Active Directory, allowing you to easily review your AD structure. By clicking on different objects, you can navigate through different AD levels and jump between users and groups as needed.
Managing permissions through a central platform is beneficial in terms of security, transparency and efficiency. Consequently, we recommend the use of tenfold‘s interfaces and workflows for any adjustments to accounts and privileges in connected systems.
tenfold regularly syncs with all connected systems and will therefore notice and identify changes made directly in the target system. So changes made in external systems are documented by tenfold. However, the audit trail for these changes includes significantly less data than for adjustments made through tenfold‘s own workflows (such as the comments left by data owners).
tenfold‘s Dashboard tracks and highlights many common errors and misconfigurations. These include: Directories with broken inheritance or directly privileged users, orphaned accounts and SIDs, empty AD groups, inactive and unused accounts, accounts without group memberships, locked accounts and guest users with active M365 licenses.
Take the Next Step
See tenfold in Action With Our Feature Video
Schedule a Live Demo With One of Our Experts
Put tenfold to the Test With Our Free Trial!