Safeguarding Digital Manufacturing Systems
The adoption of networked technologies in more and more manufacturing processes enhances productivity but exposes companies to new security threats. CTOs and CSOs need to protect their operational technology (OT) from cyberattacks. Industries from semiconductors to food processing face a never before seen level of risk. Identity & access management allows orgs to reduce their attack surface and minimize the risk of identity-based cyberattacks, ensuring continuous operations.
Adhering to Cybersecurity Frameworks
Compliance with cybersecurity standards, from NIST CSF to ISO 27001, is essential for mitigating the risks of operational disruption. IAM solutions help manufacturing firms adhere to these frameworks by ensuring comprehensive access control and providing the comprehensive reporting tools needed to prove compliance.
Important Cybersecurity Standards:
IGA Solutions Compared
Dive deep into the advantages and disadvantages of different available solutions for Identity Governance & Administration.
Enhancing Security With Automated Governance
For CTOs and CSOs, protecting critical systems from unwanted access is essential. With role-based access control (RBAC), users only receive privileges necessary for their role in the organization, preventing overprivileged users from becoming a security risk. tenfold‘s user lifecycle management automates joiner-mover-leaver processes, ensuring user access is always updated to match their current role.
tenfold integrates seamlessly with systems like Active Directory, Microsoft 365 and Entra ID, providing a unified, secure way to manage permissions across the enterprise. By automating access control, tenfold eliminates the complexity of managing thousands of user accounts while unlocking compliance with regulatory standards.
Complete Visibility
Gain full insight into access rights – from individual files to system-level oversight.
Centralized Governance
Govern access in Active Directory, Microsoft 365 and beyond through a single platform.
Fast Implementation
Achieve complete integration faster with our no-code platform and off-the-shelf plugins.
Streamlined Requests & Audits
tenfold provides a user-friendly self-service platform, allowing staff to request additional permissions or resources if they need them. All requests are reviewed and approved by data owners, with customizable approval workflows giving you full control over the self-service process.
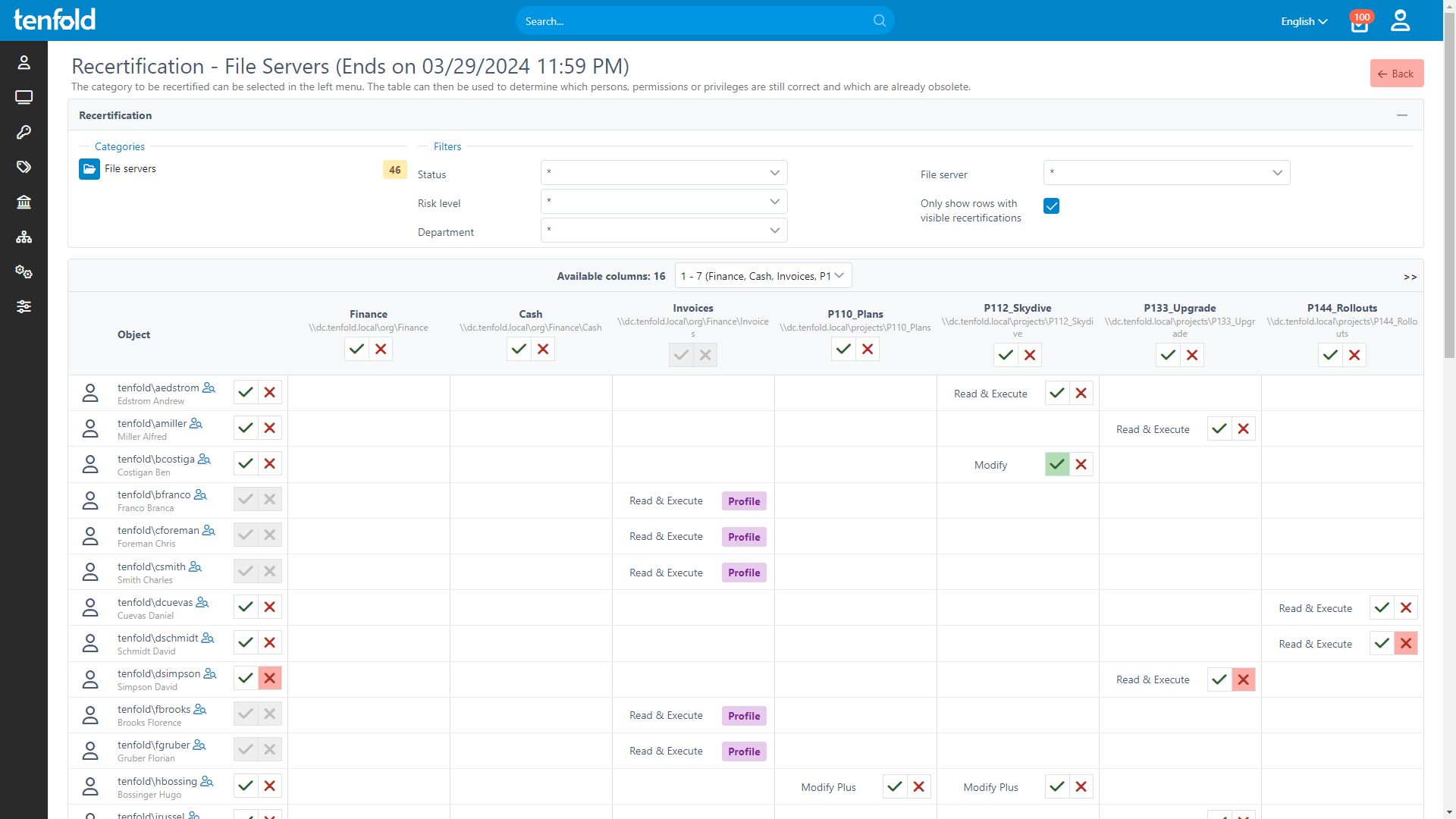
To ensure compliance, tenfold offers a streamlined audit process for user access. Data owners are regularly prompted to review permissions they have approved, with tenfold automatically collecting the necessary data, creating review checklists and implementing the results. Removing unnecessary permissions improves your overall security posture and helps you stay compliant with industry and cybersecurity regulations.
See how it works
With full visibility, central auditing and lifecycle automation, tenfold helps you regain control of IT privileges.
Watch our video overview to see it in action.
See tenfold in Action With Our Feature Video
Schedule a Live Demo With One of Our Experts
Put tenfold to the Test With Our Free Trial!