IAM Challenges in the Public Sector
Government institutions at all levels face the challenge of securely managing citizen data and critical government systems while often constrained by limited resources. The rise of E-Government initiatives has enhanced efficiency but also heightened cybersecurity threats. With cybercriminals increasingly targeting government systems and identities being their most common attack vector, agencies need robust access control measures to protect their networks and sensitive data.
Cybersecurity Legislation
Many public institutions have to comply with federal cybersecurity standards such as FISMA, the CMMC or NIST standards 800-53 and 800-171. These regulations enforce strict access control measures in institutions at the state and local level that administer federal programs like Medicare and Medicaid.
US Cybersecurity Standards
IGA Solutions Compared
Dive deep into the advantages and disadvantages of different available solutions for Identity Governance & Administration.
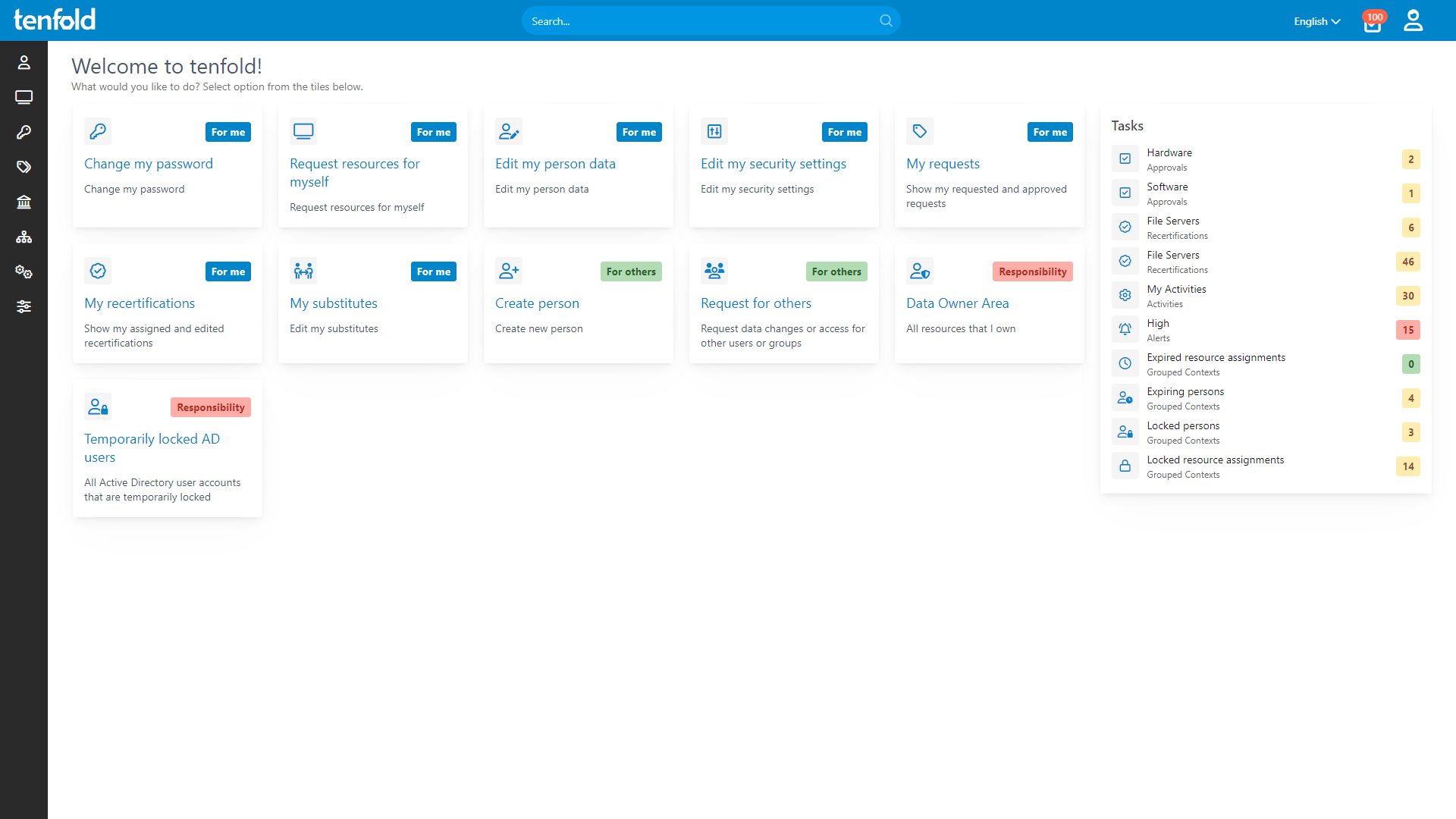
Manage Data Safely and Efficiently
tenfold enables even small IT teams to securely manage access for large volumes of data. By leveraging out-of-the-box support for Active Directory, Microsoft 365 and common workplace apps, tenfold makes it fast and easy to integrate your stack with our governance platform, allowing you to quickly reap the benefits of automated provisioning, centralized permission reporting and streamlined auditing.
Complete Visibility
Gain full insight into access rights – from individual files to system-level oversight.
Centralized Governance
Govern access in Active Directory, Microsoft 365 and beyond through a single platform.
Fast Implementation
Achieve complete integration faster with our no-code platform and off-the-shelf plugins.
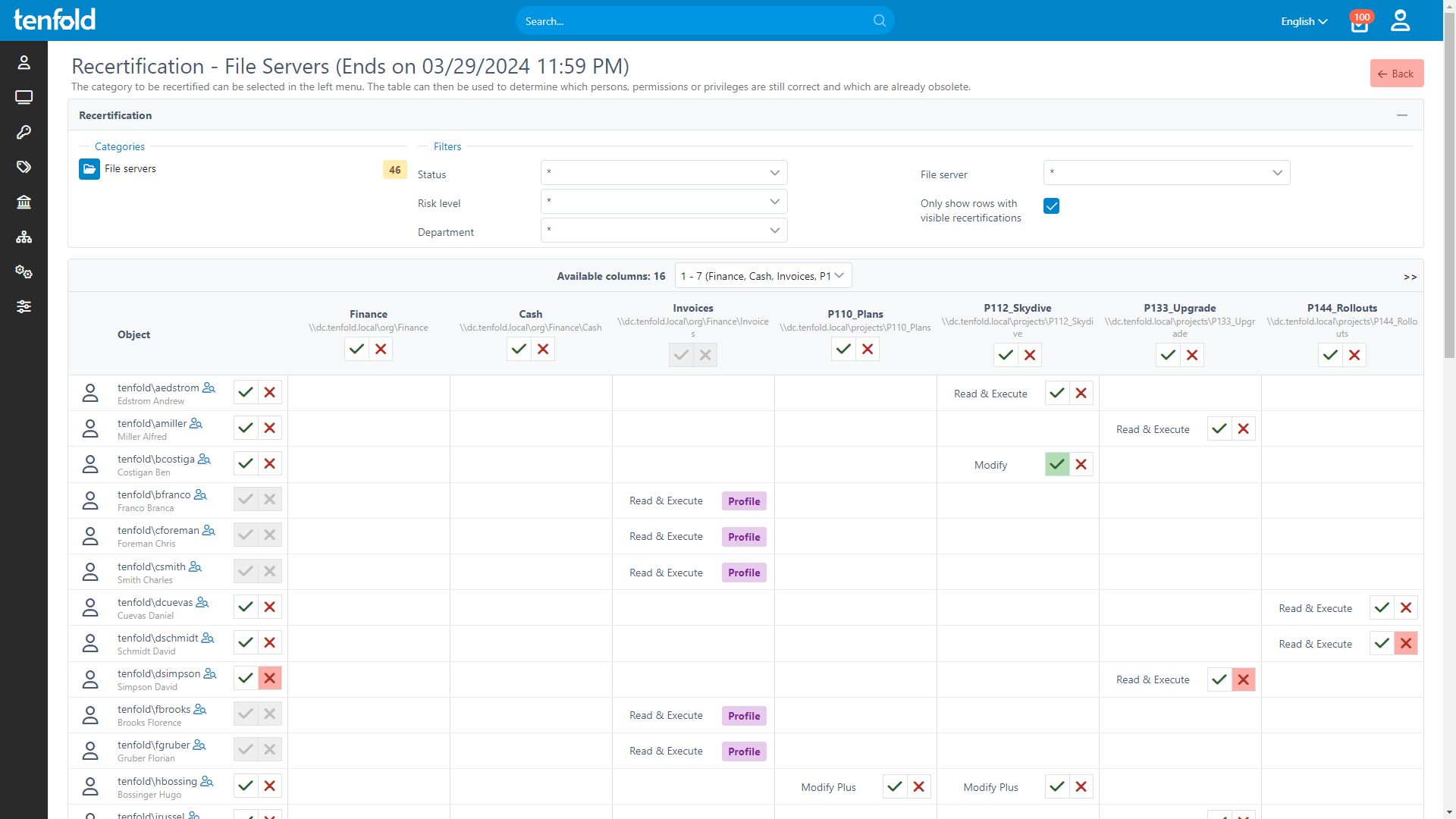
Automated Access Reviews
Compliance with state and federal cybersecurity regulations requires regular access reviews to ensure least privilege access. tenfold allows you to automate the review process – from creating review checklists to notifying data owners and updating access based on the completed review.
See how it works
With full visibility, central auditing and lifecycle automation, tenfold helps you regain control of IT privileges.
Watch our video overview to see it in action.
See tenfold in Action With Our Feature Video
Schedule a Live Demo With One of Our Experts
Put tenfold to the Test With Our Free Trial!