Information Security in Food, Drugs & Life Sciences
The food and life sciences sectors operate under stringent regulations like FDA’s Title 21 CFR Part 11 and the USDA’s HACCP guidelines. IAM systems play a vital role in ensuring secure data storage and management, allowing companies to document regulatory compliance without compromising operational efficiency.
Protecting Intellectual Property
R&D in pharmaceuticals is a costly, high-risk investment. IAM tools ensure the security of intellectual property by restricting access to sensitive data. Faced with threats like cyberattacks and employee data theft, IAM helps safeguard the competitive edge gained through innovation, keeping your discoveries safe.
IT Regulations for Food & Drug Companies
EU GMP/GxP
Title 21 CFR Part 11 (FDA)
HACCP (USDA)
IGA Solutions Compared
Dive deep into the advantages and disadvantages of different available solutions for Identity Governance & Administration.
Boost Security & Compliance
By leveraging user lifecycle automation and role-based access control, tenfold helps your company reduce cybersecurity risks. Our governance platform allows you to limit user permissions and adjust access dynamically across all connected systems: Active Directory, Microsoft 365 and workplace apps. This ensures compliance with regulatory standards while protecting sensitive data from external and internal threats.
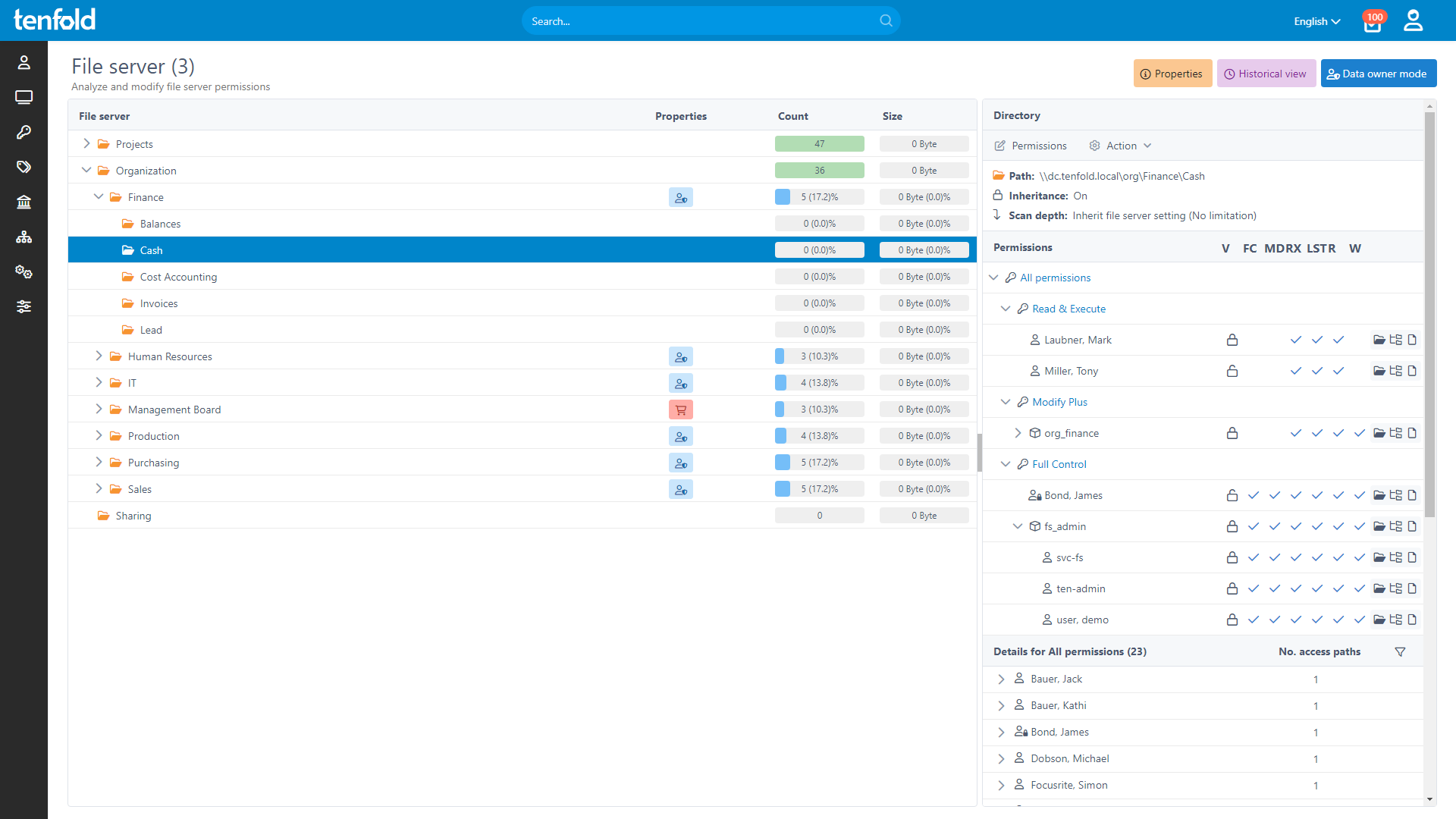
Complete Visibility
Gain full insight into access rights – from individual files to system-level oversight.
Centralized Governance
Govern access in Active Directory, Microsoft 365 and beyond through a single platform.
Fast Implementation
Achieve complete integration faster with our no-code platform and off-the-shelf plugins.
Comprehensive Reporting
Centralized permission reporting and automated access reviews ensure that outdated privileges are removed before they become a problem. With tenfold, every change to access rights is logged, providing a detailed audit trail that allows you to prove security and compliance during audits. Our comprehensive reporting and auditing toolset is essential to guarantee long-term protection against unauthorized access to critical records.
See how it works
With full visibility, central auditing and lifecycle automation, tenfold helps you regain control of IT privileges.
Watch our video overview to see it in action.
See tenfold in Action With Our Feature Video
Schedule a Live Demo With One of Our Experts
Put tenfold to the Test With Our Free Trial!