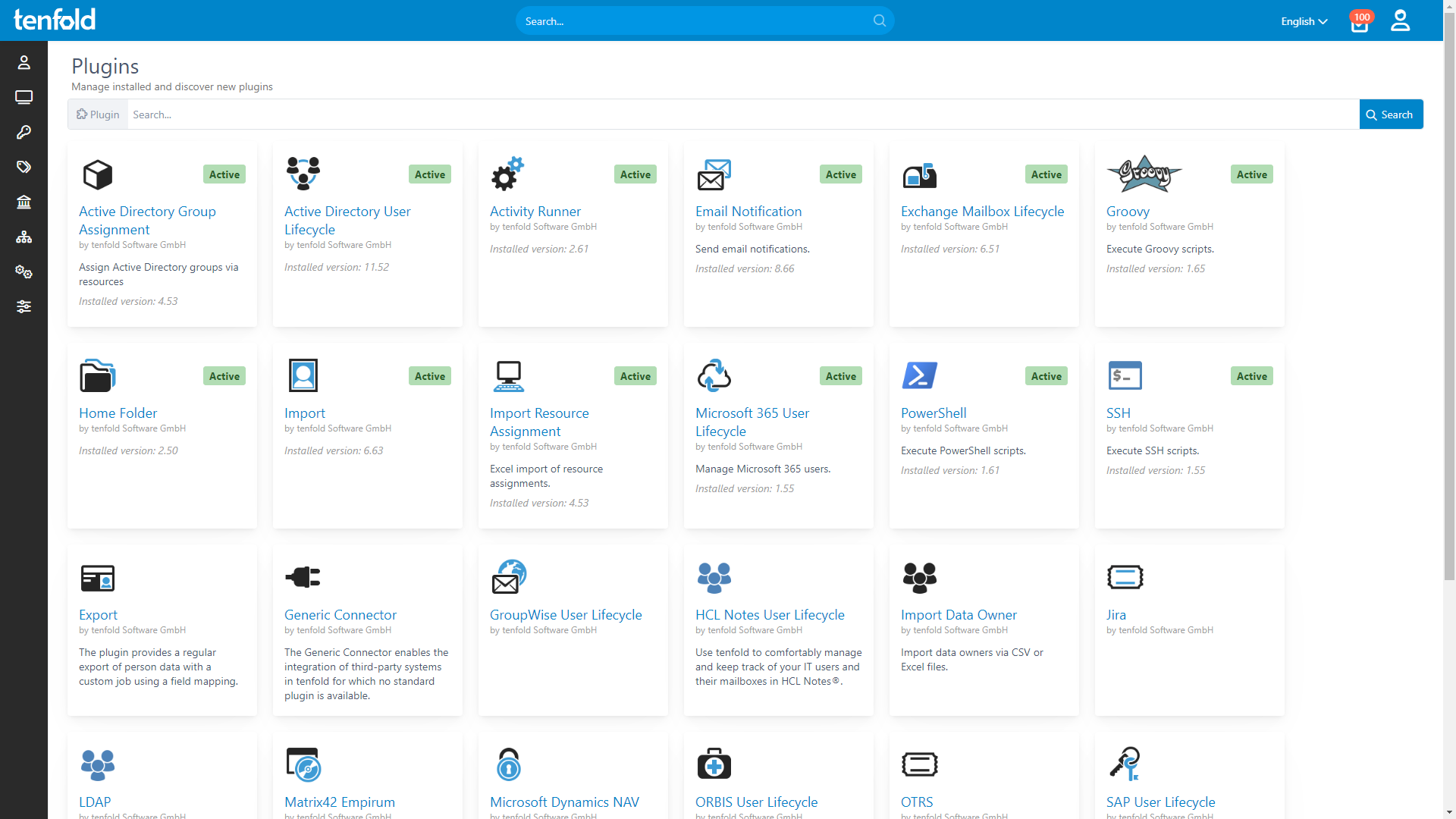
Connect Your Stack in Minutes
Forget scripting and complex setups: With out-of-the-box support for key apps and IT systems, you can fully integrate your infrastructure quickly. Activate the plugins you need, adjust a few settings and enjoy automated access governance across every system – all in record time.
Out-of-the-Box Support for the Apps You Use
From HR to ERP, groupware and helpdesk solutions:
tenfold’s no-code plugins makes it easy to connect Windows, Microsoft 365 and business apps.
Accelerate Your IAM Setup
With its no-code interface and ready-to-use plugins, tenfold drastically reduces deployment times compared to other IAM solutions. Integrate your stack faster than ever before.
Customize with Ease
Leverage SSH, Java and PowerShell integrations to expand out-of-the-box capabilities and tailor tenfold’s platform to meet your organization’s unique IT needs.
Powerful REST API
Our REST API lets you trigger workflows in tenfold from other apps, allowing for further customization of our platform.
%
75
Lower IT Workload
%
95
Faster Access Provisioning
%
98
Recommendation Rate on Capterra
%
100
Privilege Creep Reduction
Why Choose tenfold?
tenfold’s quick setup, easy configuration and powerful features make it the ideal choice for anyone looking to securely manage user accounts and IT privileges. Our all-in-one solution combines identity and data access governance into one convenient and user-friendly package.
Download our IAM Comparison
Ready to Try It Yourself?
Cloud Demo Environment
We give you acces to a cloud environment prepopulated with users and a ready-to-go tenfold instance.
Start testing right away
Enjoy our no-code UI and easy configuration
Try our automated workflows in a sandbox environment with prebuilt users & groups
Full access to all of tenfold’s features
7 day trial period
Proof-of-Value Installation
Our consultants help you set up tenfold on your network so you can test it against your own infrastructure.
In-depth test in your own IT environment
Try our no-code plugins and integrations
Turn your demo install into a real deployment (No lost work!)
Full access to all of tenfold’s features
30 day trial period
Take the Next Step
See tenfold in Action With Our Feature Video
Schedule a Live Demo With One of Our Experts
Put tenfold to the Test With Our Free Trial!