Defend Against Growing Threats
From ransomware to phishing, recent years have seen an unprecedented rise in cybercrime. As one of the most widely targeted industries, finanical services face growing challenges when it comes to providing seamless access to users while protecting critical data.
Secure, Compliant Access
Governing access to sensitive information is a core objective for the finance industry. It is also the target of keen regulatory interest. To comply with standards like SOX, GLBA or DORA, financial services need automated provisioning, central reporting and regular audits.
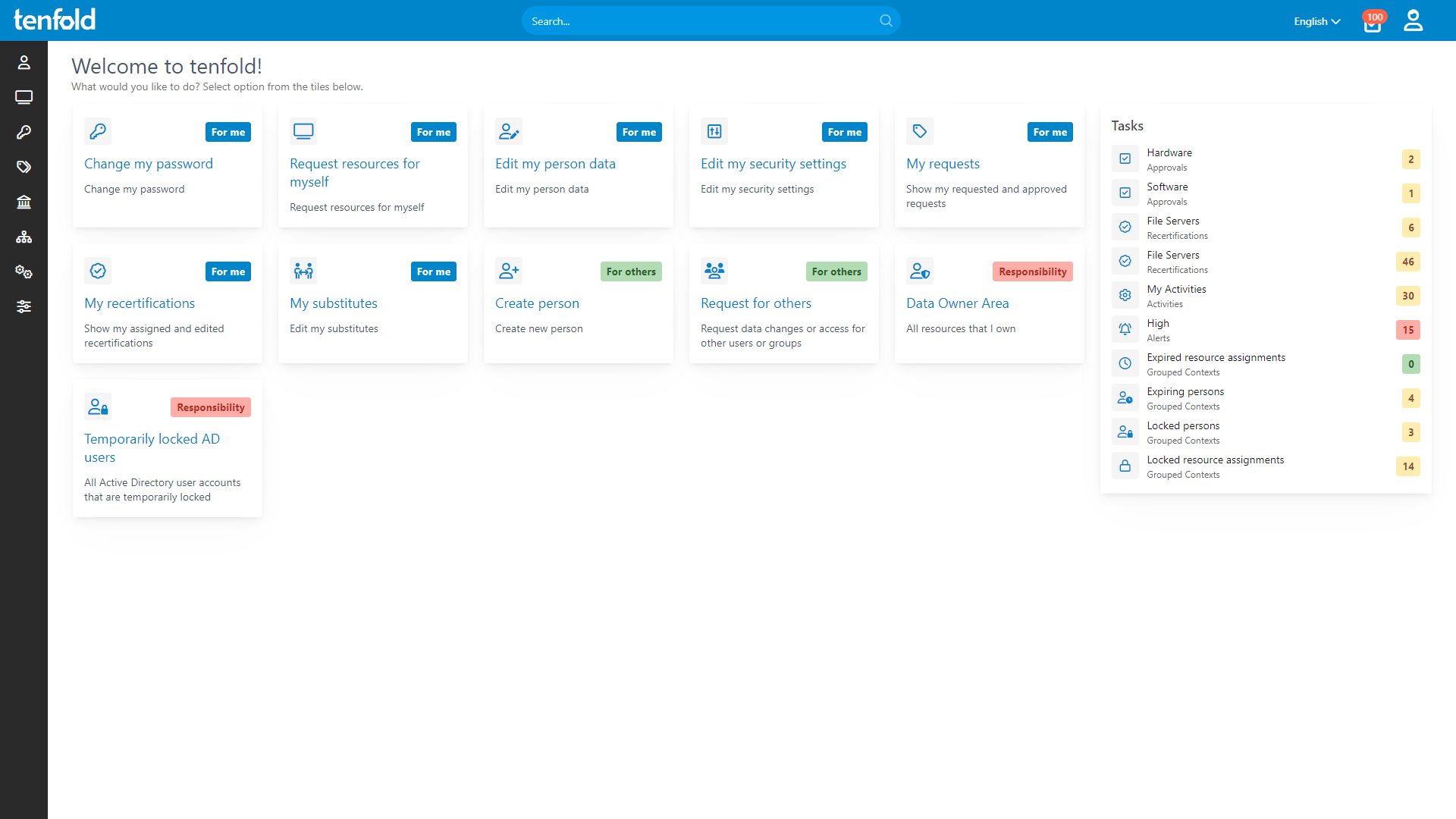
How tenfold Can Help
Segregation of Duties
Use permission roles to avoid privilege conflicts and comply with data privacy requirements.
Simplify Your Access Governance
tenfold’s no-code governance platform allows financial organizations to track, manage and audit IT permissions with ease. From automated on/offboarding to access audits and central reporting – tenfold has you covered.
Full Coverage On-Premises & In the Cloud
From on-premises systems to hybrid or cloud-only setups: tenfold makes it easy to manage access across Active Directory, Entra ID and Microsoft 365. With central orchestration, in-depth reporting and detailed audits.
Ready to Go in Record Time
While other IAM solutions need months of custom coding to set up, tenfold instantly connects to your existing IT thanks to a range of powerful plugins. This way, you’re ready to go in just a few short weeks. No scripting required!
Watch Our Demo Video
%
75
Lower IT Workload
%
95
Faster Access Provisioning
%
98
Recommendation Rate on Capterra
%
100
Privilege Creep Reduction
Trusted by Financial Services Around the World