IAM Challenges for Car Manufacturers and Suppliers
Modern cars are a miracle of engineering made up of over 30,000 parts. Each component built for performance and durability by dozens of specialized manufacturers and suppliers. But with such a complex supply chain, how can you effectively safeguard proprietary technical data?
With tenfold, governing access is easier than ever before. Our no-code platform will help you automate provisioning, monitor IT privileges and audit user access – allowing you meet growing security needs and comply with automotive cybersecurity standards like TISAX and TPISR.
Automotive Cybersecurity Standards
IGA Solutions Compared
Dive deep into the advantages and disadvantages of different available solutions for Identity Governance & Administration.
Boost Security and Compliance with tenfold Access Governance
tenfold provides a centralized platform to simplify and strengthen access governance across all business units, ensuring secure, compliant and efficient operations. Deploy rapidly thanks to out-of-the-box plugins and seamless integration. With HR data imports and a smart role mining assistant, setup is a breeze!
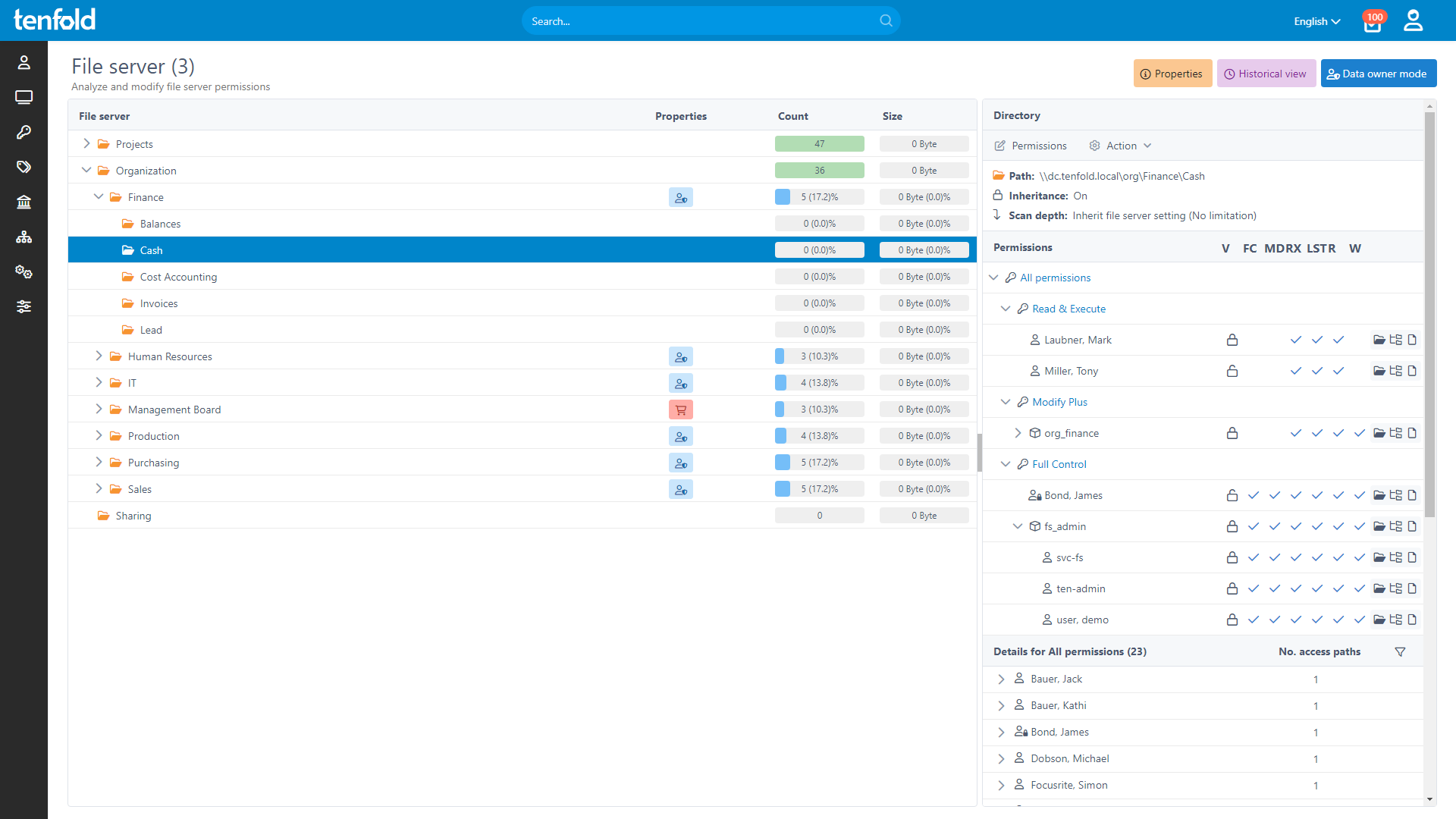
tenfold‘s access control extends across all systems, including file servers, Active Directory, cloud services and workplace apps like SAP ERP, Jira or HCL Notes- For software not supported out-of-the-box, our Generic Connector and REST API provide custom integration options, allowing you to maintain strict access control throughout the enterprise.
Complete Visibility
Gain full insight into access rights – from individual files to system-level oversight.
Centralized Governance
Govern access in Active Directory, Microsoft 365 and beyond through a single platform.
Fast Implementation
Achieve complete integration faster with our no-code platform and off-the-shelf plugins.
Flexible Reporting & Auditing
tenfold empowers organizations to implement secure, efficient permission management processes without overburdening IT teams. Designated data owners can directly assign, review and revoke access rights for resources they manage using customizable self-service workflows – eliminating bottlenecks and reducing response time.
Regular, automated access reviews ensure that permissions are always kept up-to-date, removing access that’s no longer necessary with a single click. Full audit logs track all changes and our comprehensive reporting tools provide full insight into who has access to which data – helping ensure compliance with security standards and regulatory requirements.
See how it works
With full visibility, central auditing and lifecycle automation, tenfold helps you regain control of IT privileges.
Watch our video overview to see it in action.
See tenfold in Action With Our Feature Video
Schedule a Live Demo With One of Our Experts
Put tenfold to the Test With Our Free Trial!