tenfold: The No-Code Advantage
Managing identities and access is essential for maintaining security in increasingly complex IT environments. Effective governance helps reduce risks and ensure compliance with evolving cybersecurity standards.
Conventional IGA solutions require extensive scripting to integrate, a difficult process that takes a long time and blocks valuable IT resources. This can delay setups by months or even years.
With tenfold, our no-code IGA platform, you can bypass the complexities of manual integration and jump straight to automating access governance. Our off-the-shelf plugins allow your org to achieve comprehensive IGA coverage in just weeks, not months or years.
What Sets tenfold Apart From Other IGA Solutions?
Complete Visibility
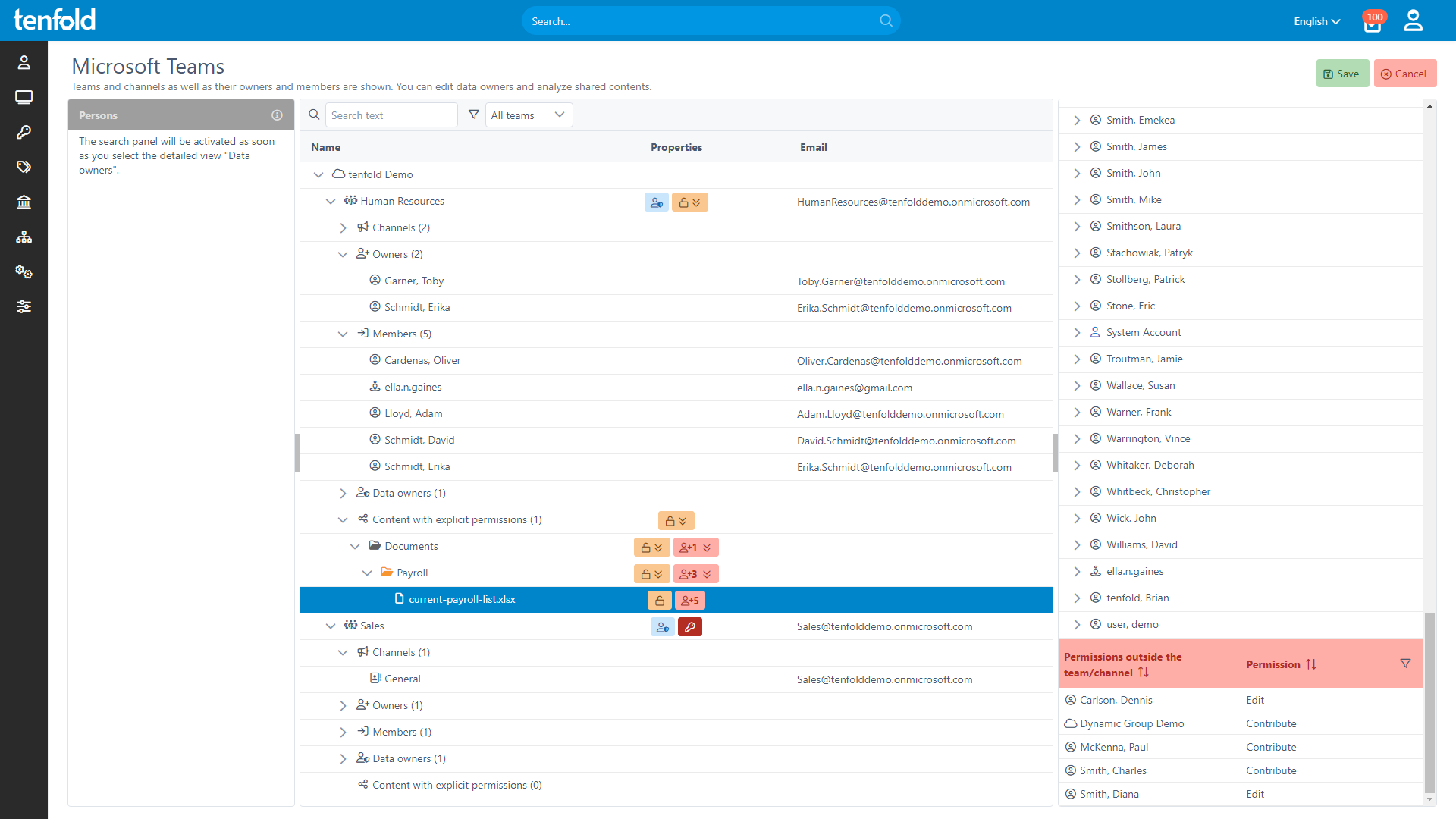
Gain full insight into access rights – from individual files to system-level oversight.
Centralized Governance
Govern access in Active Directory, Microsoft 365 and beyond through a single platform.
Fast Implementation
Achieve complete integration faster with our no-code platform and off-the-shelf plugins..
The Right Fit for Your Business
Choosing the right IGA solution is about finding a platform that covers your needs with as little effort as possible. While large corporations may need endless customization, mid-sized orgs benefit most from a streamlined, effective solution that avoids excessive overhead.
tenfold offers just that: A comprehensive IGA platform that combines powerful features and rapid deployment with minimal overhead and significant cost savings on setup and maintenance.
tenfold Strikes the Perfect Balance Between:
Data Governance solutions encompass a variety of tools meant to help you deal with unorganized data. As a short-term solution, they help admins clean up file servers and provide visualizations of group and folder structures. However, they do not allow you to automate the underlying processes, such as approval workflows, user provisioning and access reviews.
Legacy IGA solutions are designed to model the complex structure of huge businesses and public bodies. They have to incorporate a broad and often conflicting range of processes and IT systems. Enterprise-scale IGA typically comprises a bundle of several products, leading to a complicated setup process that exceeds the administrative and financial resources of mid-sized organizations.
Modern vs. Legacy IGA: What Sets tenfold Apart?
| Data Governance Tools | Legacy IGA | tenfold | |
|---|---|---|---|
| Features | Limited feature set, no flexibility | Excessive scope, highly complex | Comprehensive governance, quick & easy |
| Setup | Quick implementation due to limited scope | Heavy customization, years of setup | Up and running within weeks |
| Operation | Low effort due to missing workflows | High effort, needs team of specialists | Can be managed by one person part-time |
| App Support | No support for third-party apps | Challenging, requires custom scripts | Out-of-the-box support for your apps |
| Costs | Inexpensive, but high hidden costs | High initial costs, huge ongoing expenses | Attractive pricing & inexpensive setup |
|
|
IGA Solutions Compared
Dive deep into the advantages and disadvantages of different available solutions for Identity Governance & Administration.
Trusted by over 2,000 organizations worldwide
See for Yourself!
Our demo video will introduce you to tenfold’s full range of features. See just how easy Identity Governance & Administration can be – with the right tool.