Prevent Access Risks Before They Happen
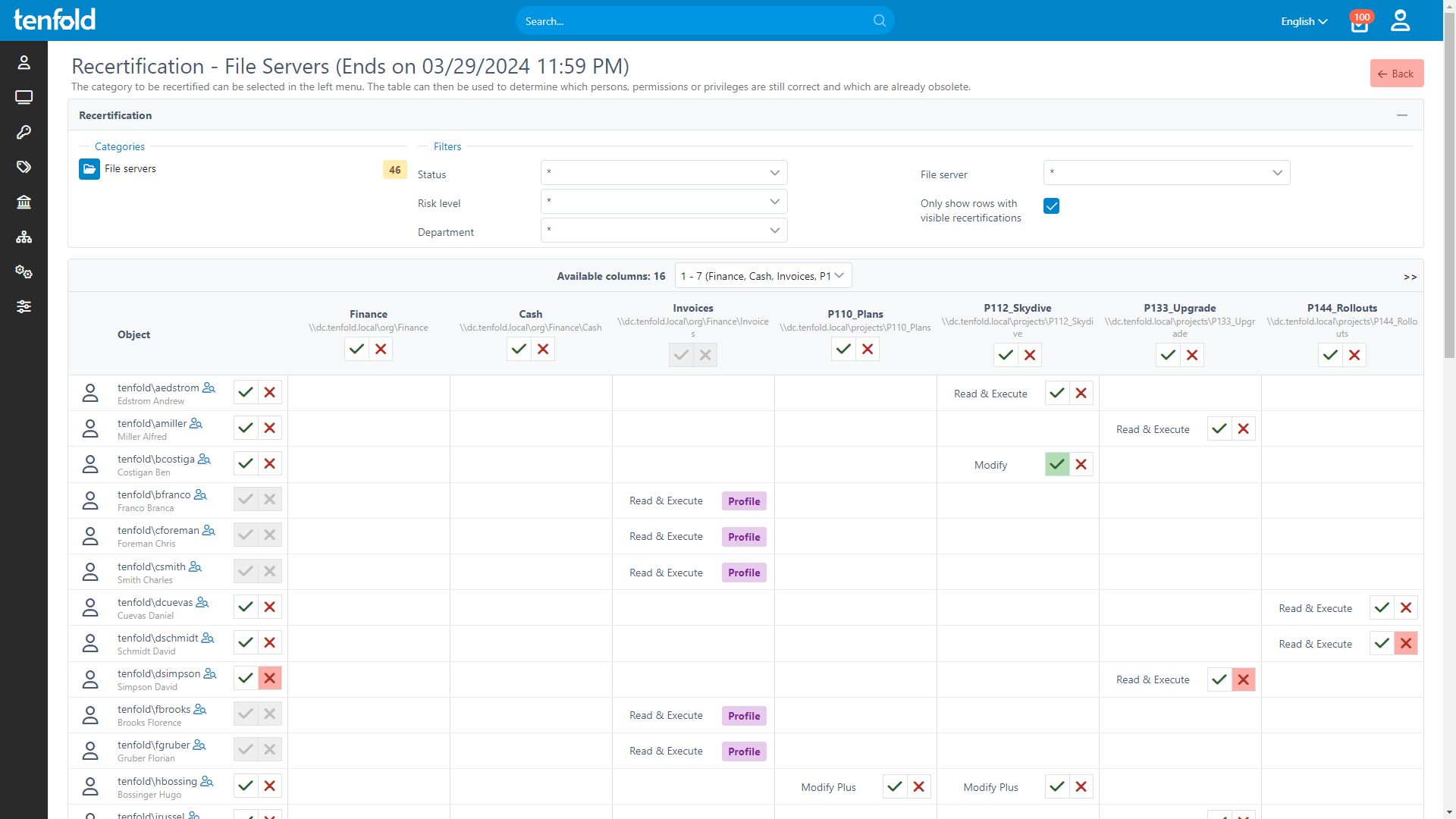
Frequent reviews ensure users don’t retain unnecessary access, minimizing security risks. With automated scheduling and notifications, personalized audit checklists for each reviewer and immediate access updates, tenfold simplifies the review process for data owners, enabling efficient privilege audits.
Ensure Security & Compliance at Every Stage
Revoking unnecessary access is critical to avoiding data breaches and maintaining regulatory compliance.
tenfold helps you tailor, execute and monitor access reviews based on your organization’s specific needs.
Customizable Audit Workflow
Adjust review scope & frequency
Review access in any managed system
Set custom escalation paths & fallbacks
Delegated Access Reviews
Enable non-IT staff to review access
Generate checklists for each reviewer
Centralized reporting on audit progress
Immediate Action on Audit Results
Automatically remove unwanted access
Log all audit actions for compliance
Maintain least privilege access long-term
Scheduled Access Audits
Set flexible audit schedules that align with your security and compliance requirements, ensuring consistent and thorough reviews.
Delegation to Data Owners
For faster and more accurate audits, assign data owners to review permissions, streamlining the process and improving security.
Minimal Effort, Maximum Impact
tenfold automatically notifies reviewers and revokes privileges that fail the audit – no manual intervention needed, which frees up IT resources.
%
75
Lower IT Workload
%
95
Faster Access Provisioning
%
98
Recommendation Rate on Capterra
%
100
Privilege Creep Reduction
Why Choose tenfold?
tenfold’s quick setup, easy configuration and powerful features make it the ideal choice for anyone looking to securely manage user accounts and IT privileges. Our all-in-one solution combines identity and data access governance into one convenient and user-friendly package.
Download our IAM Comparison
Ready to Try It Yourself?
Cloud Demo Environment
We give you acces to a cloud environment prepopulated with users and a ready-to-go tenfold instance.
Start testing right away
Enjoy our no-code UI and easy configuration
Try our automated workflows in a sandbox environment with prebuilt users & groups
Full access to all of tenfold’s features
7 day trial period
Proof-of-Value Installation
Our consultants help you set up tenfold on your network so you can test it against your own infrastructure.
In-depth test in your own IT environment
Try our no-code plugins and integrations
Turn your demo install into a real deployment (No lost work!)
Full access to all of tenfold’s features
30 day trial period
Frequently Asked Questions
The intervals between access reviews can be freely adjusted to suit your needs. tenfold also allows you to set different intervals for specific permissions in order to review access to critical systems more frequently. To prevent privilege creep and outdated permissions, access reviews should be conducted at least twice a year, ideally every three months. However, certain security standards may dictate a specific interval your organization has to follow.
tenfold allows you to designate individuals within different teams and departments as data owners. Data owners can approve self-service requests for resources under their control and they are also responsible for reviewing any permissions they have approved.
To ensure that access reviews are completed in time, tenfold provides a central overview where authorized users can track the progress of ongoing reviews across the entire organization. You can also set backup actions that automatically trigger in the event that data owner does not complete their review in the intended timeframe. Possible fallbacks range from reminders to the data owner in question to revoking all pending permissions.
The automated access review process covers all applications and services managed through tenfold. Whenever a data owner assigns a new permission, tenfold documents the change and includes it in their next audit. This ensures the ongoing control of IT privileges across all systems.
Although data owners do not have the technical expertise of IT admins, they have a much closer relationship to the people, data and assets they work with every day. This allows them to give a far more accurate assessment of who in their department needs access to what. For access reviews to represent business needs and day-to-day operations across all parts of your organization, it is therefore essential to make the review process easy to complete even for individuals without an IT background.
Take the Next Step
See tenfold in Action With Our Feature Video
Schedule a Live Demo With One of Our Experts
Put tenfold to the Test With Our Free Trial!