The Right Privileges for Every User
With automated lifecycle management, users receive the exact access they need – no more, no less. This reduces security risks, streamlines workflows and eliminates inefficiencies, enabling your team to start working faster and more securely from day one.
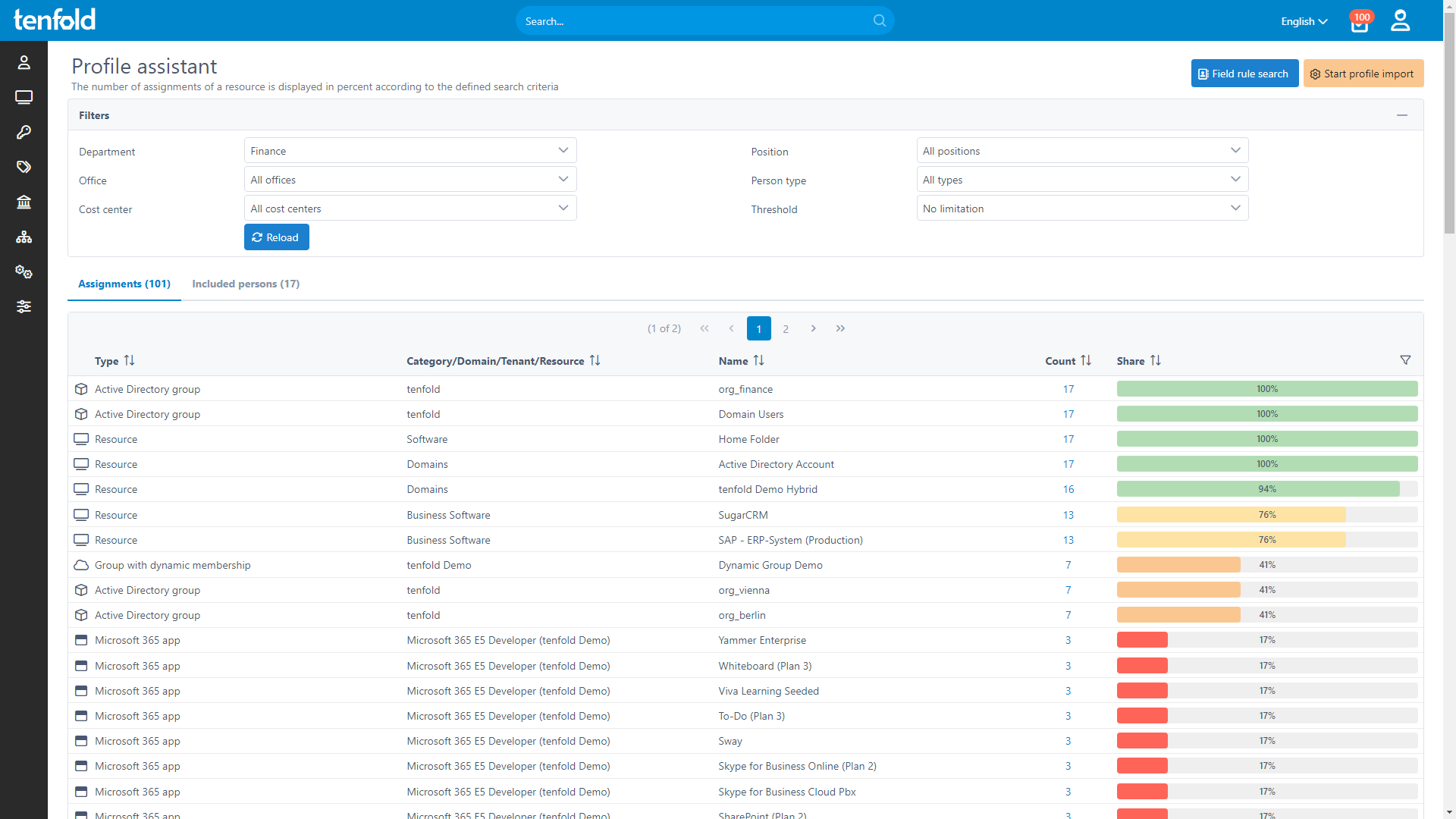
Provision Quickly and Securely
Efficient, error-free access governance is crucial to safeguarding your business.
tenfold’s lifecycle automation ensures the right access is granted to the right users at the right time – throughout their employment lifecycle.
Accelerate On & Offboarding
Seamless user onboarding in seconds
Ensure correct privileges from day one
Automatically revoke outdated access
Adapt Access as Roles Change
Update privileges as users switch roles
Detect role changes with HR integration
Enforce least privilege access with ease
Centralize Access Governance
Govern access through a single platform
Get a comprehensive view of all privileges
Save time with intelligent automation
Automated Role-Based Access Control
tenfold ensures users always have the appropriate level of access based on their role, automatically adjusting permissions whenever role changes occur, reducing the need for manual oversight.
Customizable Access Modelling
Easily create roles and policies by analyzing existing user privileges. tenfold helps you implement role-based access designed to fit your organization’s structure.
Seamless HR Integration
By integrating with your HR platform, tenfold automatically detects employee status changes and triggers provisioning or deprovisioning workflows, eliminating the need for IT intervention and ensuring up-to-date security across your organization.
%
75
Lower IT Workload
%
95
Faster Access Provisioning
%
98
Recommendation Rate on Capterra
%
100
Privilege Creep Reduction
Why Choose tenfold?
tenfold’s quick setup, easy configuration and powerful features make it the ideal choice for anyone looking to securely manage user accounts and IT privileges. Our all-in-one solution combines identity and data access governance into one convenient and user-friendly package.
Download our IAM Comparison
Ready to Try It Yourself?
Cloud Demo Environment
We give you acces to a cloud environment prepopulated with users and a ready-to-go tenfold instance.
Start testing right away
Enjoy our no-code UI and easy config
Try our automated workflows in a sandbox environment with prebuilt users & groups
Full access to all of tenfold’s features
7 day trial period
Proof-of-Value Installation
Our consultants help you set up tenfold on your network so you can test it against your own infrastructure.
In-depth test in your own IT environment
Try our no-code plugins and integrations
Turn your demo install into a real deployment (No lost work!)
Full access to all of tenfold’s features
30 day trial period
Frequently Asked Questions
tenfold‘s import plugin allows you to bulk import user data from various source systems. Simply use the provided interface to select the source and map the imported information to the corresponding fields in tenfold. User data can be imported through CSV files, SQL queries or RFC and REST calls.
As long as your HR solution supports one of these approaches, you can set up a recurring data import to automatically sync all changes made in your HR system to our IAM platform. Once tenfold receives updated information, it automatically triggers all necessary steps, such as creating new accounts, adding users to or removing them from groups, or revoking permissions.
Learn more about transferring HR data to tenfold.
During the initial setup, tenfold analyzes the organizational units in your network and automatically suggests possible roles (role-mining). To help you add default permissions to these new roles, tenfold also lists privileges held by all or most members of this group. Simply click on the permissions you wish to add to the newly created role.
You can create additional access profiles at any time through an easy-to-use interface that lets you choose members, default permissions and possible limitations. These settings can be adjusted at any time.
You can update existing roles at any time to add or remove permissions from them, for example. Changes you make are synced to all members of the role, meaning they automatically gain or lose the permissions you have changed.
To cover sabbaticals, parental leave as well as medical absences, tenfold gives you the option to temporarily deactivate a user’s accounts and permissions instead of deleting them, as you would when a staff member permanently leaves your organization. This temporary deactivation allows you to easily restore employees to their previous level of access once they return.
Take the Next Step
See tenfold in Action With Our Feature Video
Schedule a Live Demo With One of Our Experts
Put tenfold to the Test With Our Free Trial!