Access Requests Made Easy
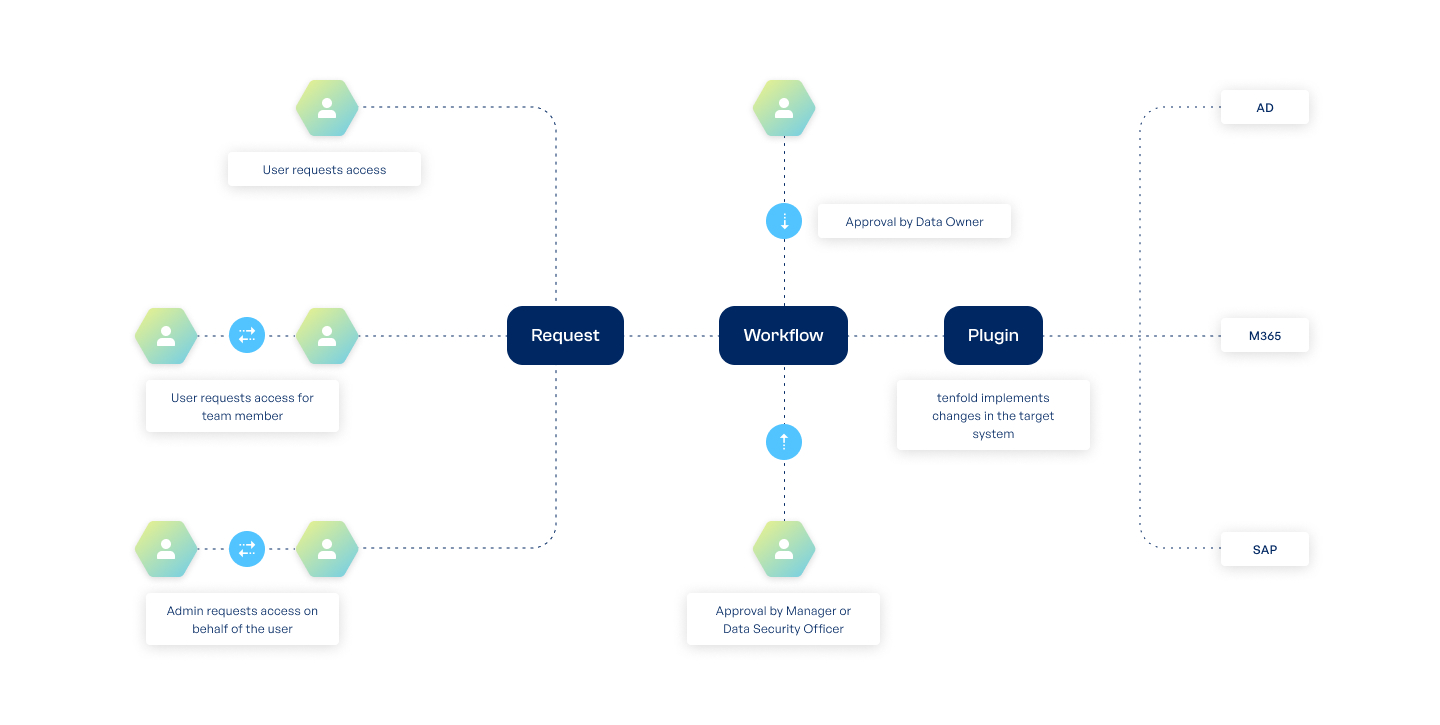
tenfold‘s self-service interface allows users to request access to additional resources whenever they need it. Requests are forwarded to the data owner assigned to a given resource, who can grant or deny access with a few clicks.
By designing their own approval workflows, organizations can decide who should be in charge of managing access to different resources.
tenfold‘s self-service interface is accessible through a user-friendly web platform where every employee is presented with the specific features available to them.
A simple, graphical editor allows organizations to design their own approval workflows for handling users’ requests.
Advantages For Your Company
Give Departments Control Over Their Data
Fewer Help Desk Tickets
Access Requests Are Fully Documented
Advantages For Your Users
Quick & Easy Approval For New Permissions
No Need to Contact IT
Self-Service Password Resets
Empower Users, Free Up Admins
Resetting passwords or granting access to additional apps and directories are some of the most common support tickets IT departments receive. Giving your users direct access to these functions saves a lot of time your IT admins can use for more important tasks.
Users can reset passwords through an external web interface where they must first verify their identity through previously established controls (such as security questions, authenticator codes or email PINs) before they can change their credentials. Self-service password resets can be activated for all systems managed through tenfold.
Keep Track of Privileges
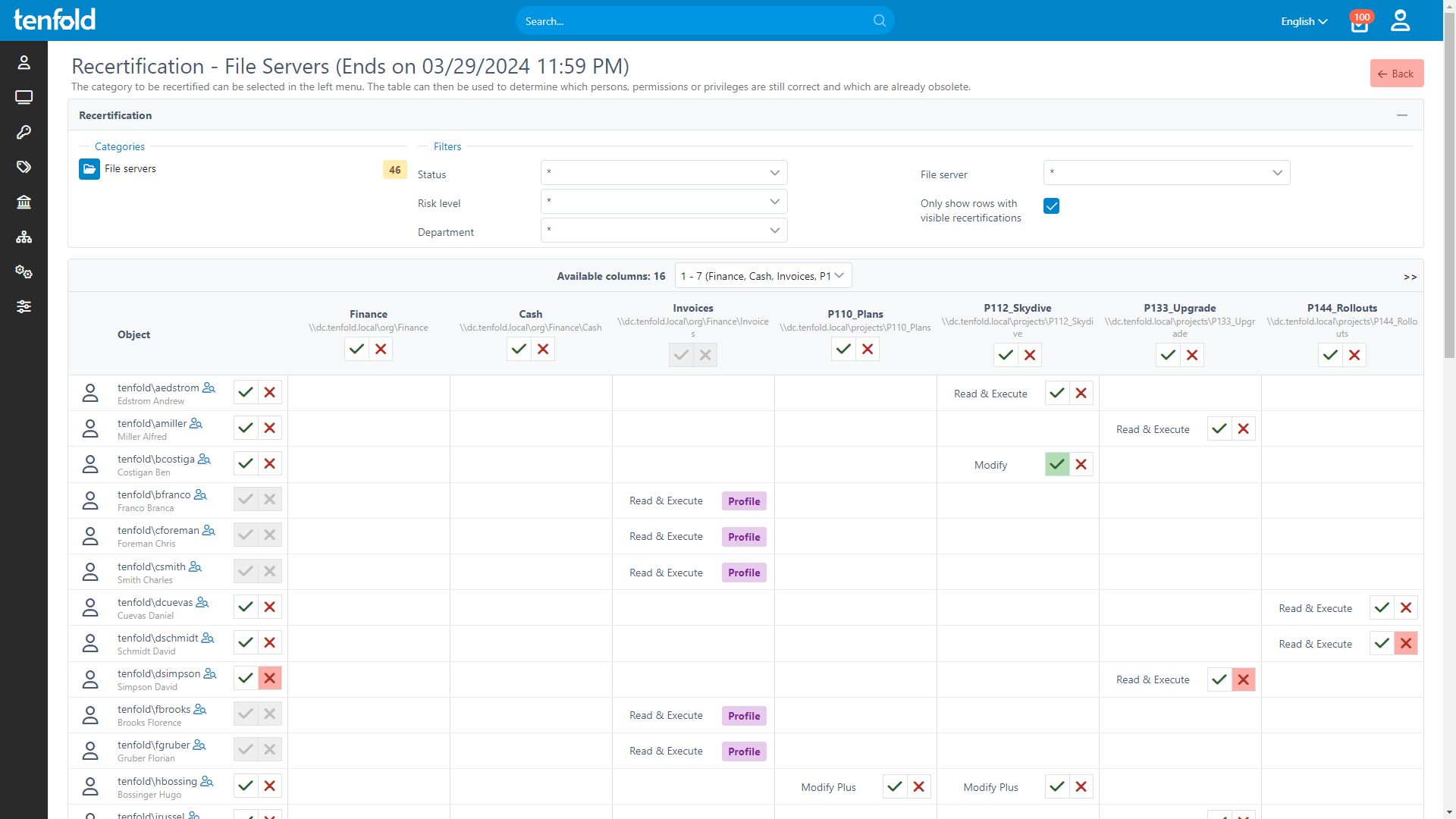
To prevent users from retaining access to resources they no longer need, data owners in tenfold have to conduct regular access reviews to check if permissions they have assigned are still in use.
tenfold compiles a list of all permissions data owners need to review, allowing them to complete the process with a few clicks. Reviewing access rights mitigates the risk of data breaches and overprivileged users.
tenfold At a Glance
All Systems
From Active Directory to Azure AD and third-party apps: Manage all IT systems through one automated platform with tenfold.
All Workflows
On/Offboarding, self-service, central reporting and regular audits. For all accounts, permissions and unstructured data.
No-Code IAM
Prebuilt plugins and no-code configuration make tenfold quick and easy to deploy, use and maintain.
Automate Routine Tasks
The combination of tenfold‘s automated user lifecycle management for baseline permissions and self-service access requests for individual rights guarantees maximum precision with minimal effort.
Frequently Asked Questions
tenfold‘s self-service platform can be fully customized to display different menu items to different groups of users. The full range of accessible features includes requesting new permissions or hardware resources as well as the option to review pending requests, edit your own user data or assign delegates. Users in leadership roles can also manage certain settings for their team members.
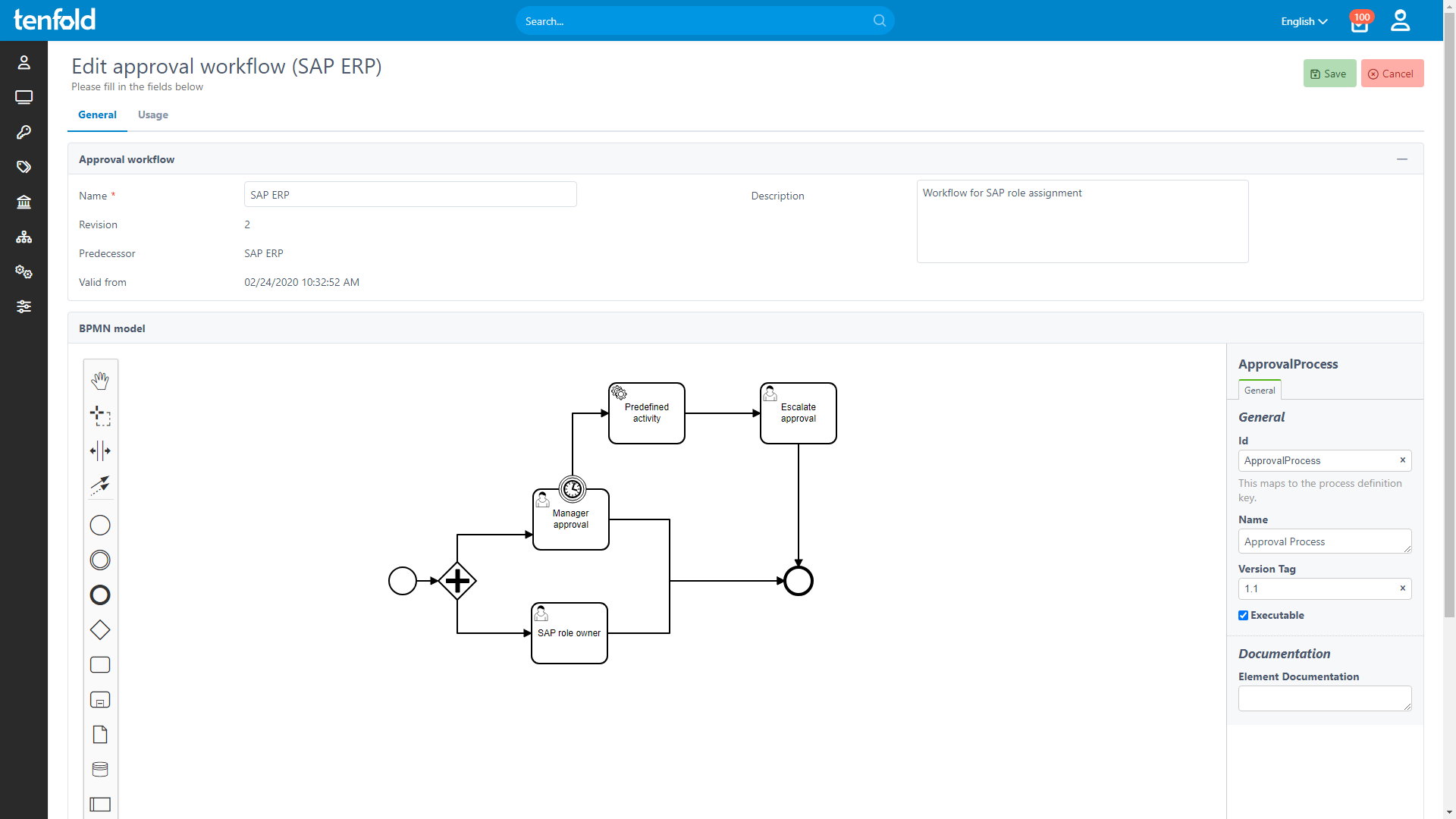
To help you create new approval workflows, tenfold provides an easy-to-use, graphical editor based on BPMN 2.0. With a few simple clicks, you can customize the data owner in charge of a given resource, the time limit for answering requests and fallback actions for unanswered requests. Options for escalating unanswered requests include email reminders as well as forwarding the request to supervisors.
Important: Workflows are not tied to a specific person, but the data owner role. If the data owner in a department changes, existing workflows are automatically updated. There is no need for manual changes.
Many organizations task their IT department with assigning any new permissions, but admins have to assess these requests at a distance and often lack critical context. Putting department leaders in control of their own data makes decisions about access both faster and more accurate.
All you have to do is define a data owner for certain parts of your network and tenfold takes care of the rest. When a user requests access to a resource under their control, data owners are automatically notified via email and can immediately grant or deny the request. To prevent misuse, data owners must verify their identity using MFA or Kerberos tokens.
Once a request has been approved, tenfold grants access to the user, documents the data owner’s decision and adds the new permission to the next access review.
To help process access requests quickly, tenfold allows you to assign delegates for data owners. Should a data owner be unavailable due to illness, travel or personal reasons, requests are forwarded to their delegate. You can also set a successor for the data owner position to ensure a smooth transition. Since workflows in tenfold are not tied to specific users, you can change data owners without having to edit existing workflows.
The self-service password reset feature supports all applications in which you manage user data through tenfold. This includes the Windows Active Directory password, as well as many cloud services and third-party solutions. Check our plugin overview for more information.
See tenfold in Action With Our Feature Video
Schedule a Live Demo With One of Our Experts
Put tenfold to the Test With Our Free Trial!