Reporting
If you’re an admin, this might sound familiar: you want to generate a report showing which users have access to specific files and folders, but quickly realize that the default tools available to you are simply not up to the job. There are no good options to track and visualize the effective permissions of users.
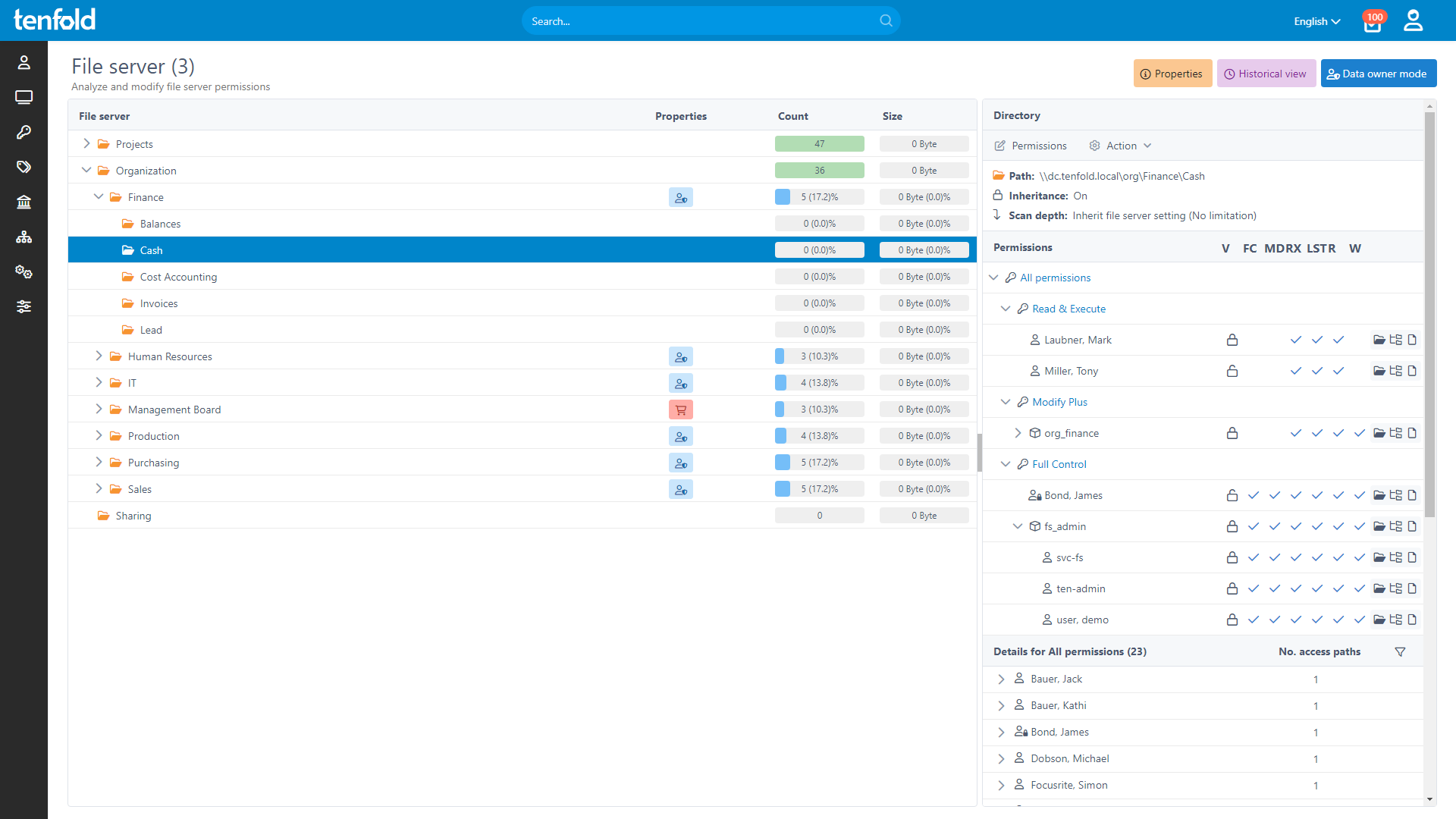
If you know this pain, tenfold is your remedy. It provides you with an intuitive, explorer-style interface, where you can simply select a folder on the file server and tenfold will show you the permission level for every user and group. It’s a clear and effective summary of access rights, including inheritances and nested groups. tenfold also allows you to select specific users or groups in order to see their permissions and level of access to shared files. To optimize the reporting process even further, automatically generated PDF reports are available via email.
Permission Management
Managing permissions on file servers using the available standard tools is a time-consuming and complex undertaking, as a great deal of manual effort is needed to set up the necessary permission groups in accordance with the best practices as recommended by Microsoft®, the AGDLP principle.
tenfold eases this pain as it creates all the infrastructure as needed automatically.
Essentials Edition
System Requirements
For a successful file server integration with tenfold, the following system requirements apply:
Access to file serve via UNC path via SMB or CIFS
Supported file servers include Microsoft Windows, NetApp®, EMC® or similar
Permissions are assigned via ACL on the basis of Active Directory objects
Service account with full access to file servers you wish to integrate with
Note: File servers based on Novell or UNIX/Linux systems (ext4, xfs, etc.) are not supported.
Self-Service & Workflows
The standard Windows tools do not support workflows for the assignment of permissions, though such workflows are essential to organizations. All compliance regulations require that the person who is responsible for a folder must give their consent before a permission for the folder can be assigned. Such approval processes must be thoroughly documented and made accessible during audits. With tenfold, data owners, supervisors and IT admins are included in every step of the workflow. When an action is required, the responsible individuals are automatically informed via email.
Dashboard
The tenfold dashboard automatically informs admins of problems concerning Active Directory® and file servers, including orphaned SIDs, circular references in groups, broken inheritances or full control privileges of non-admin users. Many of these problems can be resolved easily using the associated solution wizards in the dashboard.
Features
Report: Who has access to what folders and subfolders? (Many customizable settings).
Report: Where do users have permissions? (Including direct user permissions and group permissions, even if groups are nested).
Data history saved to tenfold database.
Admin function allows you to view and edit permissions live. Administrators can get permissions individually for each file server
Enable folders for self-service: All directories of a file server up to a certain level or individual directories can be made available for request in the self-service portal.
Determine data owners and configure workflows for approval of permission requests.
Create and delete folders, change folder names.
Automatic creation and maintenance of group structures in accordance with AGDLP, AGGP or AUUP models.
Automatic generation of required list groups to enable browsing for users.
Configurable group naming conventions.
Configurable organizational units in Active Directory for filing groups.
New permission level “Modify Plus“ to prevent folders from being accidentally moved.
Periodical import of file servers to maintain up-to-date overview of status quo in tenfold (imports can be done either on demand or at a set time).
Changes that are not applied through tenfold are logged and evaluated.