Social Engineering: What It Is & How to Prevent It
In cybersecurity, social engineering, also known as “human hacking,” refers to the use of psychological manipulation tactics to seduce people into handing over sensitive information, like logins and passwords. The acquired booty gives perpetrators access to more information, networks and systems, which they can further exploit and in consequence cause serious damage to the targeted person or organization.
What Is Social Engineering?

Believe it or not, that email from the Nigerian prince sitting in your spam folder right now, promising you millions of his fortune in return for a small upfront deposit to his account – that’s an attempt at social engineering (and it’s not even as outdated as you might think). The same goes for the email from your “bank” asking you to urgently update your payment details. It’s the phone call from “Microsoft” telling you there is a problem with your computer, and they can help you fix it. It’s your grandmother’s long-lost “nephew” who appears out of nowhere in need of money because he’s in trouble; it’s a friend request from a cloned Facebook profile; it is Anna Sorokin conning the entire New York art scene into believing she is a wealthy German-borne heiress because she wants in the club.
In other words, social engineering is a fancy term for a good ol’ scam. And scams have been around for a long time and come in many forms.
In this blog post, we will explore common social engineering techniques and take a look at some real-world cases. We will also examine the psychology of social engineering that makes it so effective and, most importantly, look at what you can do to prevent social engineering attacks from harming you and your organization (spoiler: it’s all about user education and limiting user access).
In his book “Social Engineering: The Science of Human Hacking,” author and IT-security expert Christopher Hadnagy defines social engineering as:
“The act of influencing someone to take an action that may not be in their best interest.”
Why Social Engineering?
Performing a data breach requires technical expertise: you must prepare your attack well, know how to code and how cybersecurity systems work, how to circumvent obstacles, how to place malware, and how to cover your tracks. In other words, it is a lot of work.
Social engineering, on the other hand, is a form of cyberattack that relies on deception and manipulation of humans, rather than technical hacking skills. Statistically, all it takes for a successful social engineering attack is some basic knowledge of human psychology and behavior (what gets someone to click on a link – more on that later), a phony website and an email claiming something along the lines of “Your bank account has been hacked – click here to restore your password”.

You’d think that, in this day and age, where we’re so used to receiving those kinds of scam emails on the daily, not even your great-grandma would fall for them anymore. Surprisingly, however, chances are quite high that it will work – not on everyone, but on some, and that’s enough for a social engineer to make bank.
In her speech The Dark Arts of Social Engineering, cybersecurity consultant and professional hacker Jen Fox reports an average 20% success rate for phishing emails. This means, if our faux Nigerian Prince sends out 10,000 emails containing a malicious link, 2,000 recipients will click on that link. Not too bad an outcome for almost zero effort.
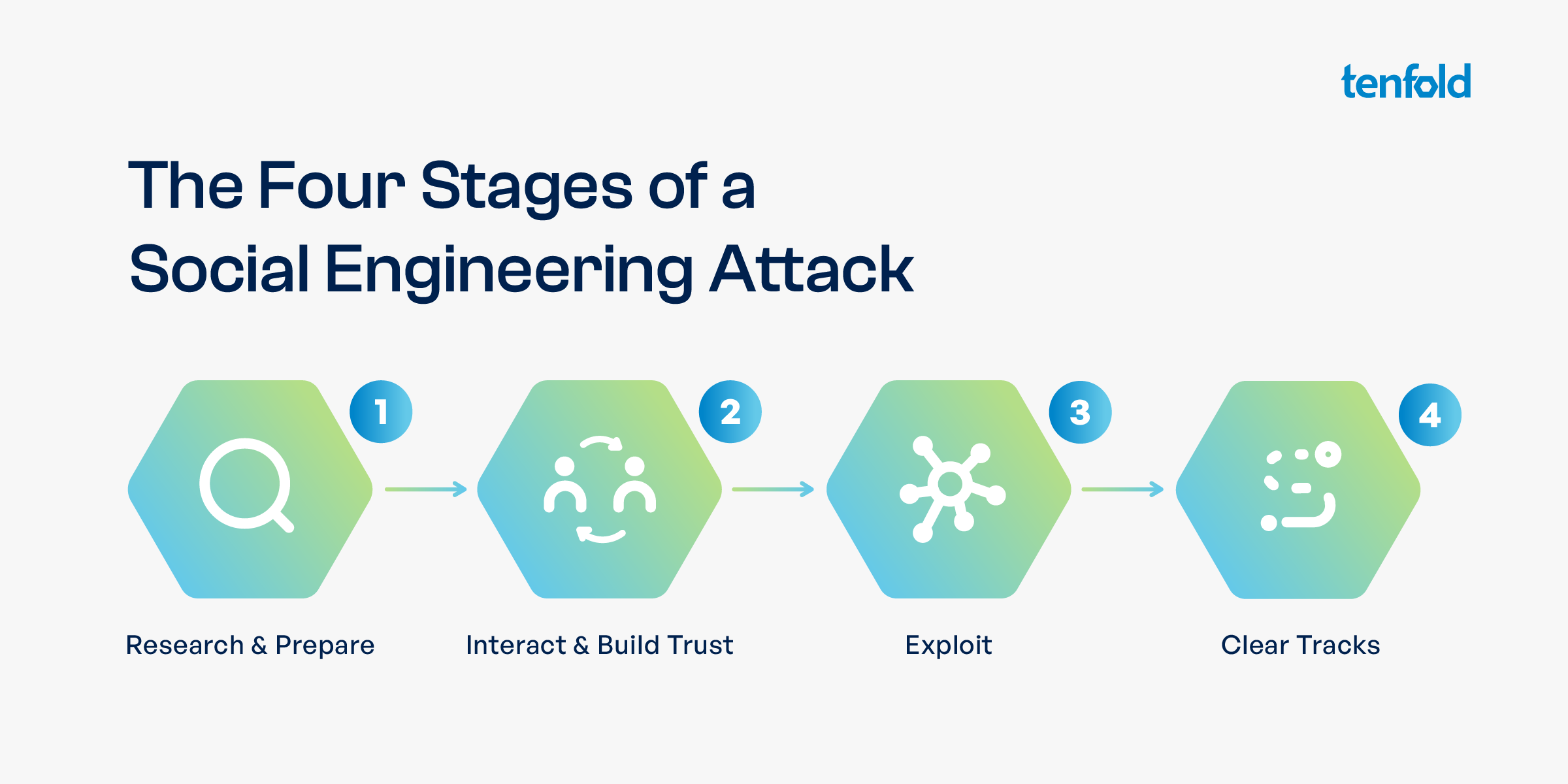
The Four Stages of a Social Engineering Attack
Regardless of the method used, every social engineering attack follows roughly the same pattern, which typically consists of these four stages:
STAGE 1: RESEARCH AND PREPARE
Gather information and prepare the attack. This involves scouting possible victims and learning more about them, for example through social media. Information of interest includes birthdates, phone numbers, work information, social activities, hobbies. Find out what position the person holds at the targeted company; decide on attack method (phishing, tailgaiting), prepare fake website if needed.
STAGE 2: INTERACT AND BUILD TRUST
Make contact with the chosen victim, get the scam rolling (example: “This is Scott from IT emailing to reset your password, please click on the following link,” or “We are conducting a survey on workplace satisfaction, would you care to answer 3 questions?”) and see if the victim latches on. If they do, gather more intel.
STAGE 3: EXPLOIT
Once trust is built, the social engineer will use that trust to request further information from the victim or that they perform a certain action to further escalate access. On a technical level, the perpetrator might harvest the stolen password from the fake website, place the spyware, trojan or other preferred malware in the victim’s system, or use the information gathered to move around in the system and find other higher-level targets.
STAGE 4: CLEAR TRACKS
Delete everything that could provide a clue as to who you are and what you did – and don’t get caught!
The larger the organization, the easier it is to build trust. In smaller organizations, where everyone knows everyone, it is much harder to pass as someone you’re not.
Psychology of Social Engineering: The Human Factor
Humans are often considered the weakest link in the cybersecurity chain because, unlike machines, they tend to be led by their emotions, which can result in poor judgement of situations. With the right strategy and knowledge, adept social engineers can milk those emotions to get the desired prize. You can bolt up your digital doors with firewalls, antivirus software and spam filters all you like, but if even one of your team members caves to the temptation or pressure of a social engineering attack, they could quickly turn into a potential insider theat and open the doors wide to malware and ransomware attacks.

Human Emotional Vulnerabilities & Social Engineering Techniques
Here are five human emotional vulnerabilities that social engineers love to pry on, paired with the complementary scamming technique that best exploits each emotion:
| Human Emotional Vulnerability | Social Engineering Technique |
|---|---|
| Trust | Pretexting: the social engineer fabricates a story intended to tickle the victim’s trust bone and get them to share sensitive information or perform an action that is harmful to them or the organization. We as humans want to trust, and we want to help. If, for example, someone – especially a person we know or have had contact with before – calls us with an issue that we are able to resolve (classic example: the CEO scam) because we’re in the right position to do so – why wouldn’t we? We assume the person on the line is telling the truth. Plus, helping another person makes us feel better about ourselves. |
| Greed | Quid pro quo is an attack form that relies on greed. The Latin phrase literally translates to “something for something”, or a favor for a favor: give me the login/files/information I desire, and I will pay you back – except that in this type of attack, you’ll get no reward, only trouble in return. |
| Fear | A typical example of a fear-based social engineering attack is a scammer disguising as your bank telling you that your account has been hacked and you should reset your password. |
| Curiosity | You’ve won the lottery! Or: you’ve been nominated for an award! Or: Your parcel has arrived! Click here! Baiting is the name of the method aimed to trigger our curiosity. |
| Anger | Like greed, its cousin anger provides an excellent breeding ground for a fertile quid pro quo attack. With some research on social media, an attacker may be able to gather enough valuable information to pinpoint who within the targeted company might qualify as a disgruntled employee. A person who feels underappreciated or unhappy at their workplace for any reason represents a high-risk insider threat. |
Who Is Likely to Be Targeted in a Social Engineering Attack?
Because the motif for many cyberattacks is financial gain, you would probably assume the most likely business target for a social engineering attack is the CEO or otherwise top-level manager who has access to very sensitive information.
The assumption isn’t wrong – later down the line, the Big Boss might indeed be the ultimate target. However, considering that the big fish are usually well guarded and require bigger nets and more planning, the juiciest initial targets for social engineering attacks are commonly found toward the bottom of the food chain, such as:
Junior staff
New staff members
HR staff
Administrative staff (non-IT)
Helpdesk & customer support
Third-party vendors & contractors
These team members often have access to multiple systems, while being more susceptible to social engineering attacks, as they are trained to assist higher-level personnel and may not (yet) be as security-aware.
Common Social Engineering Methods: Phishing & Co.
Now that we know whose emotions are likely to be exploited and why, it’s time to look at the how. It appears the Number One Method every cybercriminal, from the teenage would-be hacker acting from his parents’ basement, to the actual Russian cyber-spy, can all agree on, is phishing. According to America’s Cyber Defense Agency, CISA, 90% of all cyberattacks start with phishing.
The top 5 phishing methods used by cybercriminals to get your sensitive information are:
Email phishing: The lazy option for anyone and everyone! An email with a clicky-link that either installs the malware directly or will lead you to another fake website. Some scammers are so lazy, they don’t even bother to spellcheck their emails before sending – because they don’t have to! High success rate at the cost of little effort guaranteed!
Spear Phishing: A more targeted variation of phishing that requires research and preparation on the criminal’s side. Spear phishing targets one particular person (or group) in an organization and uses information that is of interest to that person or group, based on their job position or on interests scavenged from social media, to shape the attack. The goal is to extract login information and passwords from the victim.
Vishing, which stands for “voice phishing”. A typical vishing attempt is the call from Microsoft’s helpdesk telling you that there is an issue with your PC and they would like to help you resolve it by establishing a remote connection. Another widespread example is the “CEO fraud” scam, also referred to as “Business Email Compromise” (BEC), where cybercriminals pose as high-level executives and request urgent wire transfers of funds, usually targeted at HR or accounting staff. According to the IBM Cost of Data Breach Report 2023, this tactic has caused damages of 4.67 million US-dollars to companies worldwide.
Smishing: Phishing via SMS, for example a phony healthcare institution requesting you to click on a link in the SMS to view your test results.
Whaling – A specific type of phishing attack aimed at the “big whale” of the company, a high-level executive like the chief financial officer. Unlike Herman Melville’s Captain Ahab, however, who skipped the shrimp and went straight for the whale, the social engineer will act with more caution and collect many shrimp on his way.

Social Engineering Examples
The following three real-life social engineering attacks took place within the last ten years and caused immense damage to the affected victims:
- Facebook and Google Spear-Phishing scam. In 2013, Lithuanian national Evaldas Rimasauskas set up a fictitious computer manufacturing company. Over the span of two years, he and his associates email-phished employees at Google and Facebook into transferring $100 million dollars into fraudulent bank accounts. This con is regarded as the largest social engineering attack to date (that we know of).
- Department of Labor impersonation attack. In this highly sophisticated phishing attack, the perpetrators cloned emails and websites to lure users into disclosing their Office 365 credentials.
- Russians spear-phishing attack on Ukraine. In 2022, Microsoft warned of a spear phishing campaign by Russian hacking group Gamaredon aiming to incapacitate the Ukrainian government and NGOs and thereby prevent them from being able to respond to emergencies. The attack used malware-infested phishing emails.
The Role of Artificial Intelligence in Social Engineering Attacks
Do you remember the famous scene in Terminator 2: Judgement Day, where one Terminator (the good one, played by Arnold Schwarzenegger) faces off his nemesis, the evil liquid metal T-1000, in an unparalleled social engineering phone battle?
In the scene, young hero John Connor calls home from a pay phone, but soon suspects that something is wrong – and rightly so. The T-1000 has murdered his foster mother and taken on her persona in order to lure John back home and kill him. The Terminator – the good one, who is with John in the phone booth – takes the phone and, perfectly emulating the boy’s voice, tricks the T-1000 on the other line into making a foolish mistake, thereby blowing his cover.

Eerily, with the continuing development of deepfake technologies, the dystopian future James Cameron envisioned in his 1991 sci-fi epic does not seem so far-fetched. While murder hopefully isn’t part of anyone’s real-life social engineering masterplan, the scene does predict how skilled social engineers could make use of AI to aid their scamming goals.
Using only 3 seconds worth of original audio, tools like Microsoft’s text-to-language model VALL-E, for example, are able to perfectly reproduce a person’s voice, including sound and intonation. So, theoretically, if you have a 3-second recording of your boss’s annual Christmas party speech, you could easily put together a string of sentences to use in a Vishing scam against your own personal nemesis at work. (A scam of this sort did actually happen to a UK Energy company in 2019, where criminals used AI-based software to impersonate a chief executive’s voice and asked the CEO to transfer $243,000 dollars to a “Hungarian account”. The scam worked, and the CEO was fired).
Soon, AI-based social engineering attacks will be able to incorporate hyper-realistic video clones into their schemes as opposed to just voices. This means anyone’s face or voice can be used in a social engineering attack, and everyone is a potential victim.
Likewise, ChatGPT & co. have helped to make AI-driven phishing campaigns significantly more sophisticated. For one thing, AI helps those social engineers whose mother tongue is not the target language to produce perfectly phrased scam emails. Furthermore, AI can analyze vast amounts of data to further personalize these phishing emails, making them even more convincing and tailored to the victim.
How to Prevent Social Engineering Attacks
Since we know that humans present the greatest risk factor in organizations, the key to preventing social engineering attacks is blindingly obvious: employee training. It is absolutely essential that employees know how to recognize a social engineering attack and how to best react to it.
As an employee, here’s your list of DOs and DON’Ts when it comes to social engineering awareness:
ALWAYS ask for ID if someone you don’t know is calling or at the door.
NEVER hand out your password!
Know that IT staff will never ask for your password; not over the phone, not via email, not ever.
Don’t be afraid not to hand out information if you are unsure. Do not allow fear to lead you. If it smells fishy, listen to that gut feeling and simply ask for a number to call back on. Then, double check with your manager or with IT personnel if the call was legitimate.
Watch out for out-of-character questions. Why would “Bob” from accounting be so adamant to learn your dog’s name?
Do not plug in USB drives you randomly found in the building (but do report them to your manager or IT department).
Be aware of what you’re saying, to whom, and where. Do not share sensitive company assets with friends, family or strangers.
Beware of who may be looking at your laptop screen if working remotely at a café or on the train/plane/bus.
Reduce your digital footprint. There are 5.3 billion internet users, of which 93% (or 4.95 billion people) use social media, which means this is the number of people who can access the information you share online. Places like Instagram, Facebook & Co. are excellent intel resources for social engineers.
For this very reason, don’t make your date of birth, dog’s name or favorite pub your password.
Do not click on suspicious links or respond to emails from outside of your organization, unless you are expecting them.
Remember that all information is valuable to someone! The more personal information is shared online, the more leverage the social engineer has on you.
And here’s your list of DOs and DON’Ts on a corporate level:
Use antivirus software.
Use a firewall.
Invest in penetration testing.
Define and implement a strong password policy.
Have a corporate security policy – and stick to it!
Have an incident response plan in place.
Train staff on how to identify social engineering attacks, how to treat sensitive data and what your security policy is all about: Google’s Phishing Quiz is a good resource.
Use drive encryption on company laptops in case they get stolen.
Use multi-factor-authentication (MFA).
Shred documents.
Follow a zero trust approach: never trust, always verify.
Restrict access to a minimum (Principle of Least Privilege).
Access Management in M365: Best Practice Guide
Everything you need to know to manage cloud privileges in Microsoft 365 – from built-in tools to essential best practices!
Prevent Social Engineering Attacks with IAM
Even with all these safeguards in place, AI has seriously raised the bar for cybersecurity defenders. The likelihood that a social engineering attack will be successful is now greater than ever. So, besides ensuring that your employees know how to recognize a social engineering attack and can react to it accordingly, the second key to preventing social engineering attacks is implementing a solid access management strategy. What this means is that you must restrict user access to folders and systems down to the bare minimum (least privilege). No user should have more rights than needed to perform their job – the least privilege approach is a cybersecurity best practice for good reason.
Example: Let’s assume a social engineer has gained access to an employee’s account at your organization through a phishing attack. The attacker now has access to all the files and information the captured account has access to. It is therefore crucial that your system is set up in such a way that makes it as difficult as possible for the perpetrator to escalate their level of access by moving around in the system – however, if users have more access than they should, the attacker can move around freely.
Unfortunately, it is still common practice in organizations to grant blanket access rights to user accounts. This is because it is a time-consuming and difficult undertaking to tailor permissions to each user’s job responsibilities and to keep track of stale permissions using only the available Microsoft tools. And it doesn’t help that many companies are understaffed, especially in the IT departments. So, as users move between departments and hop on and off different projects, they collect privileges on the way which are never retracted (privilege creep).
If you have no idea who in your organization has access to what, who granted it and why, then your organization is at immediate risk for a social engineering attack.
The remedy: the identity and access management software tenfold is designed to automatically keep track of all user privileges across systems and to ensure they are withdrawn accordingly as people come and go, change departments or assume project work. tenfold allows you to govern and automate user access to systems like Active Directory, Azure AD, Microsoft 365 and many more. With one click, the application allows you to produce an access report providing you (and auditors) with an overview of who has access to what, since when, and how long for. So, even if the Terminator makes it past the gate, he’ll have nowhere to go once he’s inside.
Interested? Watch our video demo to get a better understanding of how tenfold works and how it can help you stay on top of those stray privileges.
Our No-Code Solution Makes IAM Easy.
Start Your Free Trial Today!