What Is Identity and Access Management? The Beginner’s Guide to IAM
Identity and access management (IAM) is a field of cybersecurity that governs user accounts and IT privileges in an organization. Simply put, identity & access management ensures that the right people have access to the right resources. It enables seamless access for your staff while keeping sensitive data protected from unwanted access. Done right, IAM helps organizations boost productivity, improve their security posture and stay compliant with privacy laws and security regulations.
What Is Identity and Access Management?
Identity and access management is an area of cybersecurity that deals with the administration of user accounts (identities) and their permissions and privileges (access). In IT environments, permissions govern everything from which files a user can open to which applications they can use and which areas of the network they can access. Therefore, assigning the right privileges to each user is essential to a safe and productive IT environment.
Organizations typically start out administering privileges manually. However, the more users, devices and applications are added to the network, the more difficult it becomes to maintain visibility and govern access effectively. Eventually, organizations reach a size at which their IT team can no longer keep up, leading to widespread problems such as:
Slow and time-consuming onboarding
Stale or overprivileged accounts
No visibility into current access
At-risk sensitive data
Endless flood of access requests
Overwhelmed helpdesk staff
Inability to audit privileges
Delays to strategic IT tasks
To address these issues and ensure that user privileges are assigned quickly, correctly and without manual intervention, companies eventually turn to automated solutions for identity and access management. Dedicated IAM platforms allow organizations to centralize and automate the governance process, from user onboarding to self-service requests, in-depth reporting and streamlined auditing.
Sub-Categories Within Identity and Access Management
It’s important to understand that the field of identity and access management can itself be divided into different areas of interest – with specialized solutions that focus on one or more of these pillars. Some tools in the IAM space focus on workforce administration, while others deal with customers or CIAM. There are solutions that specialize in offering a smooth, secure and centralized login experience and there are tools that help orgs determine what a user should be allowed to do once they are logged in.
The different areas within identity and access management are:
Authentication & Identity Verification
Multi-Factor Authentication
Conditional Access Policy
Single Sign-On
Biometrics
Identity Governance & Administration
User Lifecycle Management
Role-Based Access Control
Access Reviews
Self-Service
Centralized, In-Depth Reporting
Object-Level Visibility
Change Tracking
Audit Trail
Privileged Access Management
Secure Remote Access
Monitoring of Active Sessions
Credential Vaults
Real-time Alerts
Why Is Identity and Access Management So Important?
Without the right accounts and permissions, there is almost nothing employees can get done in a modern workplace. Users depend on their Windows accounts, email accounts, cloud accounts, accounts in third-party apps and more. At the same time, businesses store more and more sensitive data in these different applications, and the threat of data breaches and cyber attacks continues to rise.
Identity and access management ensures that only the right people can access IT resources. This way, IAM protects critical data from both external attacks and insider threats such as employee data theft. At the same time, IAM helps your IT department save valuable time by automating routine tasks like user lifecycle management and permission audits, while providing self-service features for end users.
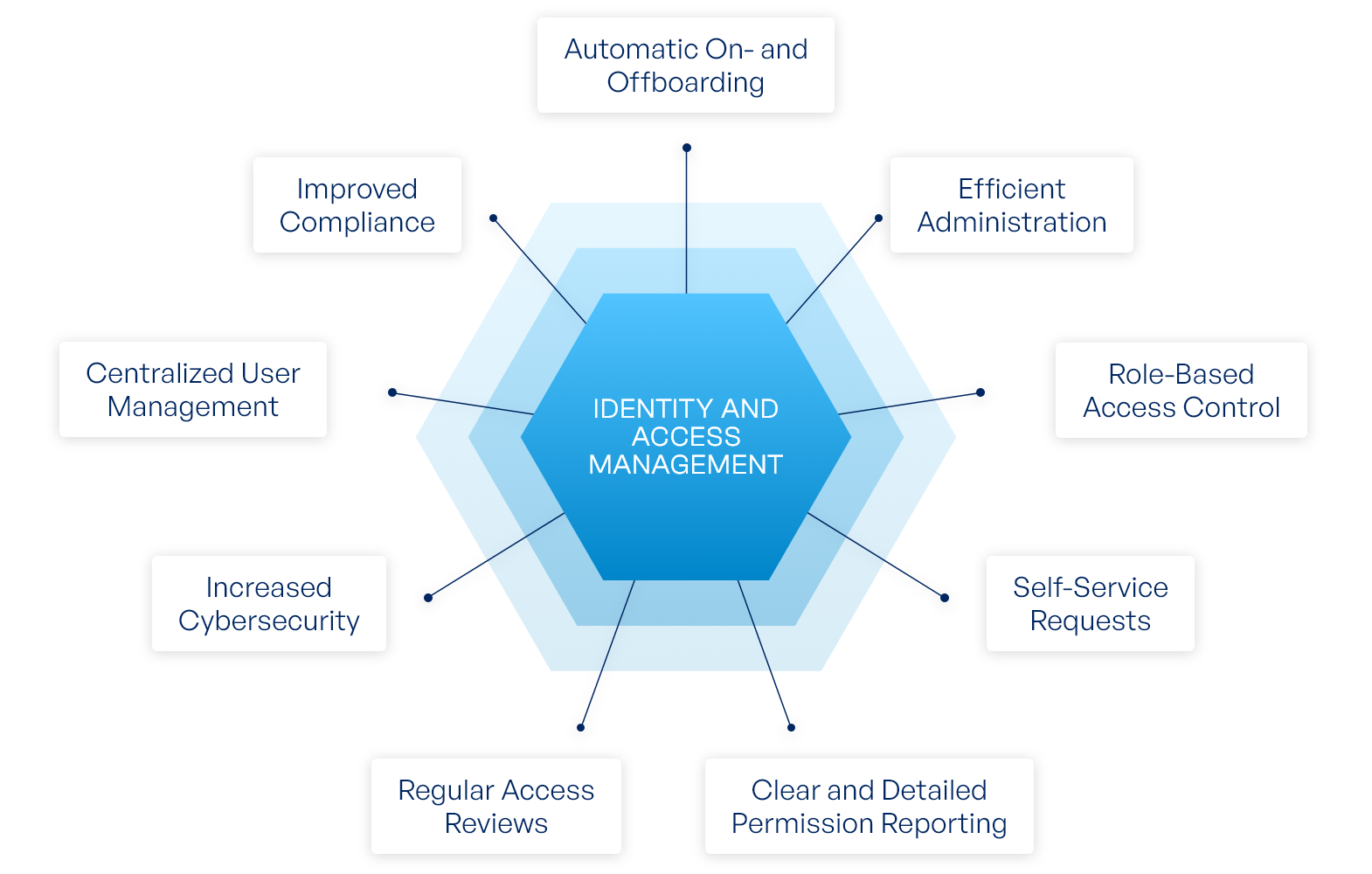
Advantages of Identity and Access Management
While identity and access management is critical to data security, this is far from the only advantage IAM brings to organizations. Managing accounts and permissions through a central, automated platform drastically reduces the administration workload for your IT staff. Even common helpdesk tickets like password resets or access requests can be outsourced to the IAM system, allowing your admins to focus on more important tasks and long-term projects.
Meanwhile, IAM helps your end users get to the data they need faster and easier since they can request new permissions directly through the platform instead of sending out tickets or emails. That means fewer delays in the day-to-day operations. And with every change documented automatically, the business is always in control of who has access to what.
Benefits of IAM:
Accurate access for every user
Automatic provisioning and deprovisioning
Compliant user management and auditing
Protection from internal and external threats
Clear overview of effective permissions
Fewer support tickets
Fewer delays for end users
Less time wasted for admins
Is Identity and Access Management Mandatory?
There are various laws, industry norms and security standards that require organizations to restrict access to sensitive data and actively manage accounts and permissions. It is not mandatory to use an identity and access management system to meet these requirements. However, there is no practical way to comply with these regulations without the support of an IAM system.
Without IAM software, it would take astronomical effort to enforce least privilege access, perform regular user access reviews and document all changes to accounts and permissions. So while identity and access management is not explicitly mandatory, there is simply no way around IAM for organizations with more than a few dozen IT users.
Laws and standards that contain identity and access management requirements:
How Does Identity and Access Management Work?
Identity and access management lets organizations control which users have access to which files and systems. On a technical level, there are two separate steps that govern access to IT resources:
Authentication: Users verify their identity by entering their credentials (username and password) and completing multi-factor authentication. If the verification is completed successfully, the user is allowed into the system. In the case of central identity providers like Active Directory and Azure AD, they are also logged into various connected apps (single sign-on).
Authorization: Once a user authenticates their identity, they are authorized to perform specific actions. What a user is allowed to do depends on which permissions have been assigned to them by the admin. In Windows environments, authorization is determined by checking an account’s security identifier against the access control list of an object.
Learn more about the difference between authentication and authorization.
Account Provisioning
When an admin creates a new account, the IAM system automatically assigns the correct permissions, groups and organizational units. Identity and access management determines which privileges to give to which user through an access control model known as role-based access control: First, organizations define the intended permissions for different business roles, such as people working in different departments.
The identity and access management software then provides new accounts with the permissions matching their role: employees in the sales department receive the permissions of the sales role, employees in marketing receive marketing permissions and so on. This process also applies when the role of a user changes: when a new role is assigned, the person is given all privileges of their new role and loses all permissions associated with their old role.
Identity and Access Management in Microsoft Environments
Learn how to manage access securely and efficiently with our best practice guide to the technical and organizational aspects of IAM in Windows networks.
Self-Service For Users
Roles offer a quick and easy way to assign default permissions. However, users often need additional permissions for projects, substitutions or special tasks. Normally, this involves annoying emails and phone calls, but with an identity and access management solution, users can request additional permissions through a self-service interface.
Requests for new privileges are forwarded to the data owner who controls the resource in question, i.e. a team lead or manager within the department in question. This allows departments to manage access to their own data without the need for IT staff to get involved. Not only does this mean less work for your admins, it also leads to faster and more accurate approvals.
Reporting Tools For Admins
Which users have access to which files? Without an identity and access management solution, this simple question is surprisingly hard to answer. To get the full picture, admins need to compile permissions from various systems. This is especially tricky when it comes to figuring out access to unstructured data like the documents stored on file servers or in SharePoint.
With the standard tools provided by Microsoft, there’s no way to see exactly which files a user can access or vice versa: that information is obscured by nested groups and complex folder structures. Identity and access management breaks this information down for you to offer a clear, concise report of effective permissions on a user and item level.
For example: While Microsoft 365 normally provides no insight into which files your users are sharing and with whom, tenfold offers a handy summary of shared files across Teams, OneDrive and SharePoint that lets you filter between different apps, internal or external accounts and more.
User Access Reviews
Successful identity and access management not only involves providing users with the privileges they need, but also removing outdated and unnecessary permissions. Access rights that have served their purpose must be revoked to prevent users from accumulating more and more permissions over time, which threaten the security and confidentiality of critical data. This gradual accumulation is also known as privilege creep.
The only way to ensure that users only hold permissions they need is to audit IT privileges regularly. During this user access review, the data owners who have approved the permissions either confirm or delete them. While this kind of oversight cannot be fully automated, an IAM platform makes the audit process quick and convenient by tracking which rights need to be audited, compiling them into clear checklists, notifying data owners of pending audits and documenting the results.
Identity and Access Management Features
Aside from the main features of an IAM system, there are many other functions and concepts surrounding the topic of identity and access management. This short IAM glossary provides an overview of the most important terms.
| IAM Feature | Explanation |
|---|---|
| Provisioning | The process of providing a new user or account with the correct permissions and resources |
| User Lifecycle | The lifecycle of a user account from creation to ongoing adjustments and deletion, mirroring an employee’s on- and offboarding |
| Role | A set of permissions tailored to a specific group of users, like members of the same department |
| Single Sign-On | Authentication process that is valid across multiple applications |
| Self-Service | Platform that allows users to request permissions or services like password resets |
| Workflow | An adjustable provisioning or approval process, for instance to determine who reviews self-service requests |
| Data Owner | Non-IT staff with the authority to approve requests or audit permissions |
| Access Review | Recurring permission audit designed to remove unnecessary privileges |
The 5 Steps of Implementing an Identity and Access Management System
Even if you understand how identity and access management works in theory, you may be wondering: How do you put IAM into practice? What are the steps an organization needs to take to implement an IAM system and what are the challenges and pitfalls to look out for during IAM implementation? In this section, we will look at a step-by-step approach to IAM projects, from picking an IAM system to installing, configuring and maintaining it.
Choosing a Solution
Before you can install an identity and access management solution, you obviously need to choose the product you want to use. There are many different providers on the market, each with their own strengths and weaknesses. If you have never shopped for IAM software before, it’s important to do your research and find a system that suits your needs instead of simply picking the biggest brand name.
Important questions you should be asking yourself while evaluating IAM systems include: Does this software cover all the features I need? Can it be connected to the applications we use? Does it match our budget? And can it be used effectively with the amount of IT staff we have?
The amount of effort it takes to operate enterprise-scale solutions is a common roadblock for IAM projects in mid-sized businesses: the deployment turns into a multi-year project, many planned features are abandoned halfway through and the whole process ends up wasting more time than it saves. To avoid this nightmare scenario, it is important to choose a software that fits the size of your organization.
You can find more tips for choosing the right solution in our IAM comparison.
Connecting Your Applications
An identity and access management system serves as your central hub for managing users and permissions. In order to fulfil this role, it needs to be connected to all your different apps and systems: Windows services like Active Directory and file servers, cloud apps like Azure AD and Microsoft 365 as well as third-party apps like SAP or HCL Notes.
Although the ability to interface with other applications is essential for a functioning IAM platform, most solutions don’t allow you to connect with other systems out of the box: They provide an interface framework but expect you to create your own plugins through custom programming and extensive scripting.
This time-consuming process delays IAM projects and drives up costs through the need for external consultants. The good news is: You can avoid plugin programming entirely! tenfold offers prebuilt plugins with no-code configuration. Simply choose the interfaces you need from our plugin library, adjust their settings through the GUI and you’re good to go.
Importing Users and Data
Before an identity and access management solution can administer the existing accounts in an organization, it first needs to import and analyze the users, permissions and information architecture of the network.
Setup assistants and smart features help make importing data a painless process. Aside from importing accounts from various systems, you can also import current file server structures. However, it’s important to make sure that you still follow best practices like AGDLP and access based enumeration. Additionally, tenfold lets you automatically sync changes from the HR system, allowing you to manage the user lifecycle directly through your HR platform.
Defining Roles
In order to automate account provisioning and the assignment of access rights, organizations first need to set the intended privileges for their users. An IAM system cannot decide which users need access to what, but it can help you pick appropriate permissions by looking at users’ current rights.
When you create a new role, tenfold automatically shows you which permissions are most common among the users you selected. This lets you quickly identify and add default permissions shared by all or most members of a role, such as access to the department’s directory on the file server. The process of creating permission roles by analyzing users’ current permissions is also known as role-mining.
Changes and Optimizations
IT environments are constantly changing. New users come and go, devices and applications are added, the network architecture changes. Because of this, IAM implementation is not a one-time task, but an ongoing project: The software needs to be continually updated and adjusted to match your organization’s changing needs.
The easier an IAM system’s initial setup is, the easier it will be to make changes later on. This kind of flexibility is important to ensure you continue to benefit from the advantages of identity and access management without too much maintenance work from your administrators.
tenfold IAM: Your Quick, Simple, All-in-One Solution
Between more and more complex IT setups, increasingly strict regulations and the growing threat of cybercrime and ransomware, there is simply no way around the topic of identity and access management for organizations that want to administer their information systems safely and efficiently. However, it is not enough to understand the features, components and advantages of IAM in theory. Ultimately, what matters is how you put these concepts into practice.
With tenfold, we have created an IAM platform that combines a wide range of features with a user-friendly interface and quick and easy setup. While other providers would have you spend months or years writing custom scripts and code, full-scale deployment of tenfold is a matter of just a few weeks thanks to our standardized plugins and no code configuration.
Can IAM really be that easy? See for yourself by signing up for a free trial! Or read what the independent analysts at KuppingerCole had to say about tenfold.
KuppingerCole Executive View: The Expert Opinion on tenfold
An independent report by the analyst firm KuppingerCole confirms that tenfold lives up to its goals: Principal Analyst Martin Kuppinger and his team describe tenfold as a well thought-out IAM solution tailored to the needs of mid-market organizations.