NTFS Permissions: Best Practices for File & Folder Permissions
Learn how to manage NTFS permissions securely and efficiently with the 15 most important best practices for NTFS permissions.
NTFS Permissions Best Practices
Follow a consistent policy: Make sure all admins follow the same approach when it comes to naming conventions and folder structure.
Always use groups: Assign permissions to Active Directory groups rather than individual users.
Nest groups to model permission roles: Don’t add users directly to permission groups. Instead, add permission groups to an overarching role group and add users to that.
Maintain a clean folder structure: Keep root clear, create as few top-level folders as possible, don’t let anyone outside of IT add more top-level folders.
Set permissions at the highest level: Set permissions at the top level of your folder structure and let them propagate down to reduce the amount of permissions you need to manage.
Avoid breaking inheritance: Do not break permission inheritance unless absolutely necessary. If a folder needs different permissions than its parent, it may be easier to move it up a level.
Avoid deny permissions: Avoid using deny permissions as they will make your permission structure more complex.
Use the most restrictive permission possible: Limit users’ permissions as much as possible. Do not grant Modify if Read is enough to do the job.
Avoid giving users Full Control: Full control lets users edit NTFS permissions, which a normal user does not need to do. Modify is the highest permission level a normal user should need.
Enable access-based enumeration: ABE makes folder navigation easier by hiding directories a user cannot access.
Pay attention to list rights: If you enable access-based enumeration, make sure users have the List Folder Contents permission for parent objects or they cannot navigate to a subfolder even if they have access to it.
Create a process for access requests: Establish a clear process for users who need additional permissions, making sure the request is documented and approved.
Document permission changes: From user requests to updates to your permission structure, document any noteworthy changes.
Audit permissions regularly: Review NTFS permissions to ensure user access remains appropriate even as responsibilities change.
Use the right tools: Managing NTFS permissions by hand is time-consuming and leads to errors. Use the right tools to help you automate user lifecycle management, govern access and audit permissions.
Permission Management Best Practices
The Principle of Least Privilege
To avoid privilege abuse, give each IT user the lowest permission level possible that still allows them to do their job. This approach is known as the principle of least privilege and is one of the cornerstones of effective data security. Enforcing least privilege access long-term requires a structured provisioning process as well as regular permission audits.
Role-Based Access Control
Role-based access control simplifies permission management by grouping together privileges needed for a specific role in the organization. For NTFS and Active Directory permissions, role-based access control can be implemented using the AGDLP principle: Create permission groups, add them to role groups and then add users to these role groups. However, it’s better to automate permission management across your entire IT using a solution for identity & access management.
User Access Reviews
User access reviews are regular permission audits designed to identify and remove unnecessary permissions. Even with streamlined on- and offboarding, users can accumulate permissions over time through requests or changing roles. Access reviews help you stop this privilege creep and eliminate access risks.
Access Governance Best Practices for Microsoft Environments
Everything you need to know about implementing access control best practices in Active Directory, from implementation tips to common mistakes.
What Are NTFS Permissions?
NTFS permissions govern access to files and folders in Windows environments that use the New Technology File System, the default file system for all modern Microsoft systems. This makes NTFS permissions one of the central pillars for access control in Windows environments.
NTFS permissions apply whether access is made locally on a device or on the network through a file share or file server. Because of this interaction, it is generally recommended to set Share permissions to a high level and use NTFS permissions to determine the effective level of access.
Learn more about the interaction between NTFS and Share permissions.
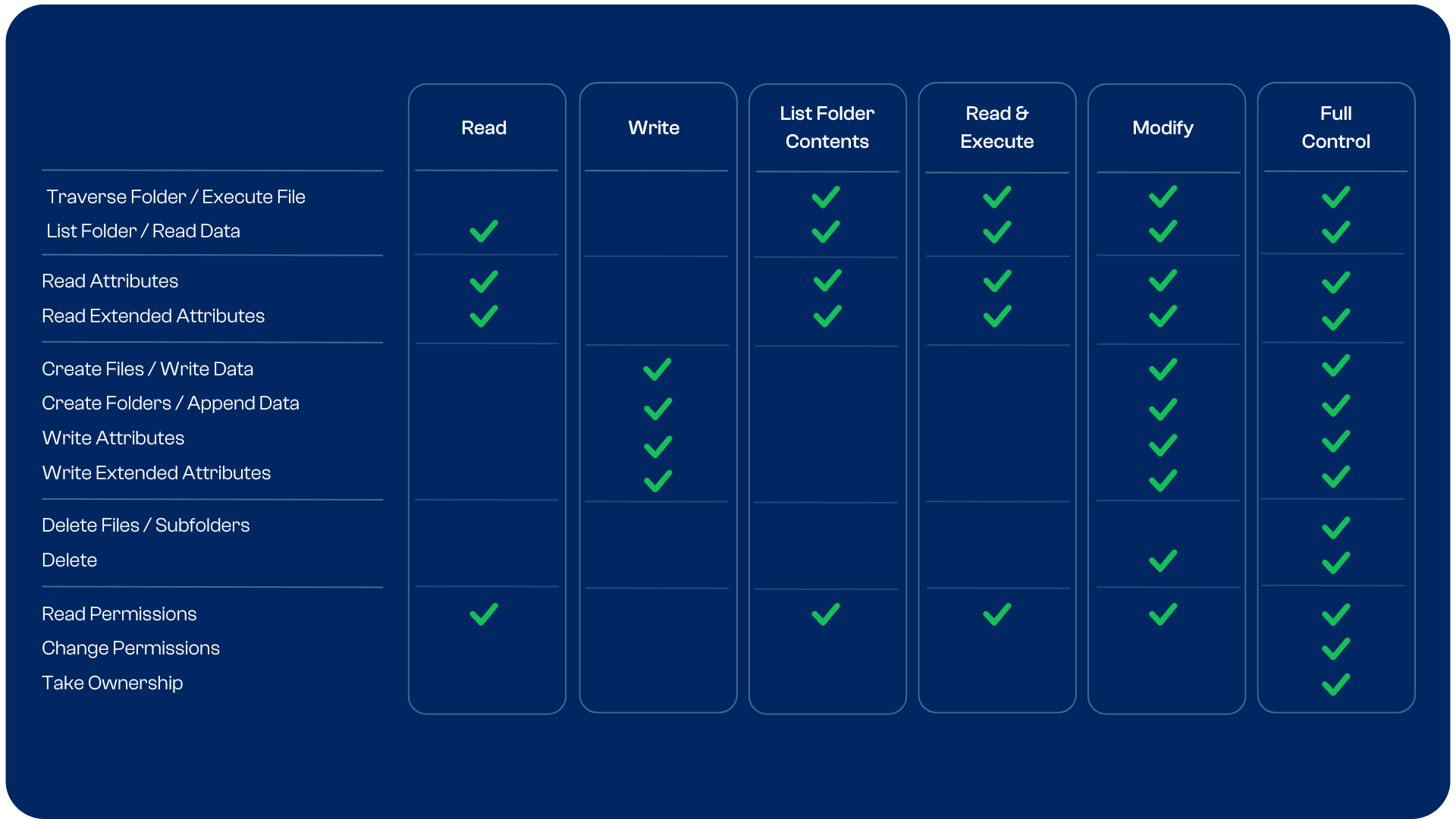
What Types of NTFS Permissions Are There?
There are six basic NTFS permissions, each of which is made up of a set of smaller advanced permissions or special permissions. You can check the table below to see which permission type contains which exact permissions.
Some NTFS permissions have different effects depending on whether they are applied to a file or folder. For example, if the “Create Files / Write Data” permission is applied to a folder, it allows the user to create new files in that location. If it is applied to a file, it allows the user to edit that file.
Here is the full list of all NTFS advanced / special permissions:
Traverse Folder / Execute File: Allows the user to navigate through a folder even if they do not have permission to open any files or folders within. Allows running a program if applied to a file.
List Folder / Read Data: Allows viewing file and subfolder names within a folder. Only affects the contents of a folder, not whether the folder itself will be listed. Allows viewing files.
Read Attributes: Allows viewing attributes of a file or folder, like “hidden” or “read-only”.
Read Extended Attributes: Allows viewing extended attributes, which depend on file and program type.
Create Files / Write Data: Allows creating files within a folder or changing, adding and overwriting data within a file.
Create Folders / Append Data: Allows creating new folders within a directory or appending data to a file.
Write Attributes: Allows changing attributes of a file or folder, like “hidden” or “read-only”.
Write Extended Attributes: Allows changing extended attributes of a file or folder, which depend on file and program type.
Delete Subfolders and Files: Allows deleting subfolders and files, even if the Delete permission has not been set on these objects.
Delete: Allows deleting of a file or folder.
Read Permissions: Allows reading permissions of a file or folder.
Change Permissions: Allows changing permissions of a file or folder.
Take Ownership: Allows taking ownership of a file or folder. Owners can always change permissions, regardless of other permissions on an object.
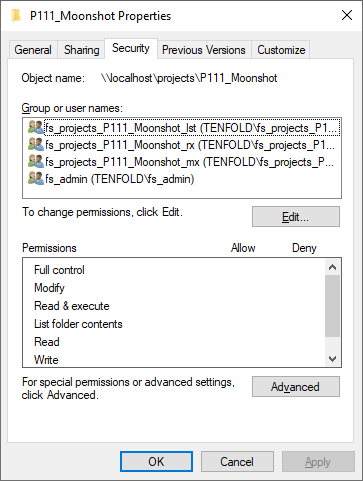
How Can I Set NTFS Permissions?
To change the NTFS permissions of an object, simply right click on it, choose Settings and switch to the Security tab, as pictured below.
However, since you need to create and manage a lot of Active Directory groups to effectively govern NTFS permissions, the majority of NTFS administration is done by managing group memberships through Active Directory Users and Computers or PowerShell. Ideally, you want to avoid manual administration altogether and automate the process through an IAM solution.
How Do NTFS Permissions Work?
Each object in Windows has an Access Control List or ACL. You can think of the ACL as a list of names and permission levels. When a user tries to access an object, Windows checks their Security Identifier (SID) against the Access Control List. If the SID of the user or one of their groups is on the list and they have the correct permission level, they are allowed access.
While NTFS permissions are generally set to allow access, they can also be used to deny access. Deny permissions are written to the beginning of the ACL and generally take precedence over allow permissions. However, the specifics of which permission overrides which are a little more complicated.
There are two important concepts you need to understand here:
Permission inheritance: To avoid having to set permissions on each individual object, NTFS permissions propagate down from parent objects to child objects by default. So if you give a user access to a folder, they will also receive access to all of its subfolders. You can break inheritance if necessary, but this is not recommended since it creates confusion.
Permission precedence: Different inherited and explicit permissions can lead to permission conflicts. In this case, explicit permissions take precedence over inherited permissions and deny permissions take precedence over allow permissions. For example, if a subfolder inherits “Deny Read” and you grant a user “Allow Read” on it, they will be allowed to read files in the folder.
How Effective Permissions Are Determined
Putting together what we know about NTFS and Share Permissions, as well as permission inheritance and precedence, let’s review the rules for how access is determined in Windows environments:
For local access to objects, NTFS permissions alone determine access.
On file shares, NTFS permissions and Share permissions determine access and the more restrictive permission takes priority.
By default, child objects inherit permissions from parent objects.
Permissions inherited from nearby objects take precedence over more distant objects (for example, one level higher vs. three levels higher on the directory tree)
Explicit permissions take priority over inherited permissions.
Deny permissions take priority over allow permissions, however an explicit allow permission will override an inherited deny permission.
NTFS: Effective Access Governance with tenfold
Even if you know all the rules and best practices for managing NTFS permissions, the real challenge is applying your knowledge to thousands of users, groups, files and folders. Managing NTFS permissions by hand is a recipe for disaster and inevitably leads to mistakes, even among diligent and hardworking admins.
The default tools of the Windows file system simply leave a lot to be desired. How can you automate IT onboarding? How can you track access on a user and object level? How can your users request new permissions if they need them? How can you review access? Unless you want to rely on spreadsheets, you need a better solution!
tenfold is your simple answer for automating permission management and access governance in Microsoft environments. From role-based access control to self-service requests and access reviews – tenfold does it all in one convenient and easy to roll out package. Book a personal demo today to learn more about what makes our no-code IAM the ideal solution for your business!