NTFS Permissions vs. Share Permissions – What’s the Difference?
Both share permissions and NTFS permissions are used to manage access to resources in Windows environments. Both permission types help you protect sensitive data and prevent unauthorized access. But what is the proper way to combine them and how do NTFS and share permissions interact? In this guide, we’ll take a closer look at the differences between share permissions and NTFS permissions and illustrate some best practice examples for mixing NTFS and share permissions in Windows networks.
What Are NTFS Permissions?
NTFS (New Technology File System) is the standardized file system for Microsoft Windows NT and newer versions of Microsoft’s operating system, replacing the earlier FAT and FAT32 file systems. NTFS permissions govern access to folders and files on Windows drives. Unlike share permissions, NTFS permissions apply both for local access to the file server and network access. That is the main difference between NTFS permissions and share permissions: The latter only apply when access is made via the network.
Setting NTFS Permissions
Setting NTFS permissions is not overly complicated, though there are a couple of pitfalls you should be aware of. Read our guide to NTFS permission best practices to learn how to avoid the 5 most common mistakes admins make. To apply NTFS permissions, right-click on a folder or file and select Properties, then navigate to the Security tab to edit permission levels for different groups. For maintenance and security reasons, you should not apply permissions to individual users.
NTFS Permission Levels
While share permissions only offer three options (Full Access, Modify and Read), NTFS permissions give you more granular control over how a user can interact with a file or folder. The level of access you define is written into the object’s access control list and checked against the SID of the user or group. By default, permission inheritance means that access rights propagate from parent to child objects, but you can disable inheritance to prevent this.
The following NTFS permission levels are the most important ones to know about:
Full control: The user has permission to change the contents of files and directories and can furthermore change system settings (e.g. permissions or ownership of the folder).
Modify: The user has permission to see, read, execute, write and delete files.
Read & Execute: The user has permission to view file contents in the folder including scripts and may execute programs.
List folder contents: The user has permission to see directories and files contained in the folder.
Read: The user has permission to see which directories and files the folder contains and can also view the contents of these files and folders.
Write: The user has permission to add files and subfolders and to write to files.
Special permissions: Additional permissions available through the Advanced Security Settings, including options like Read Attributes, Create Files or Delete Subfolders and Files.
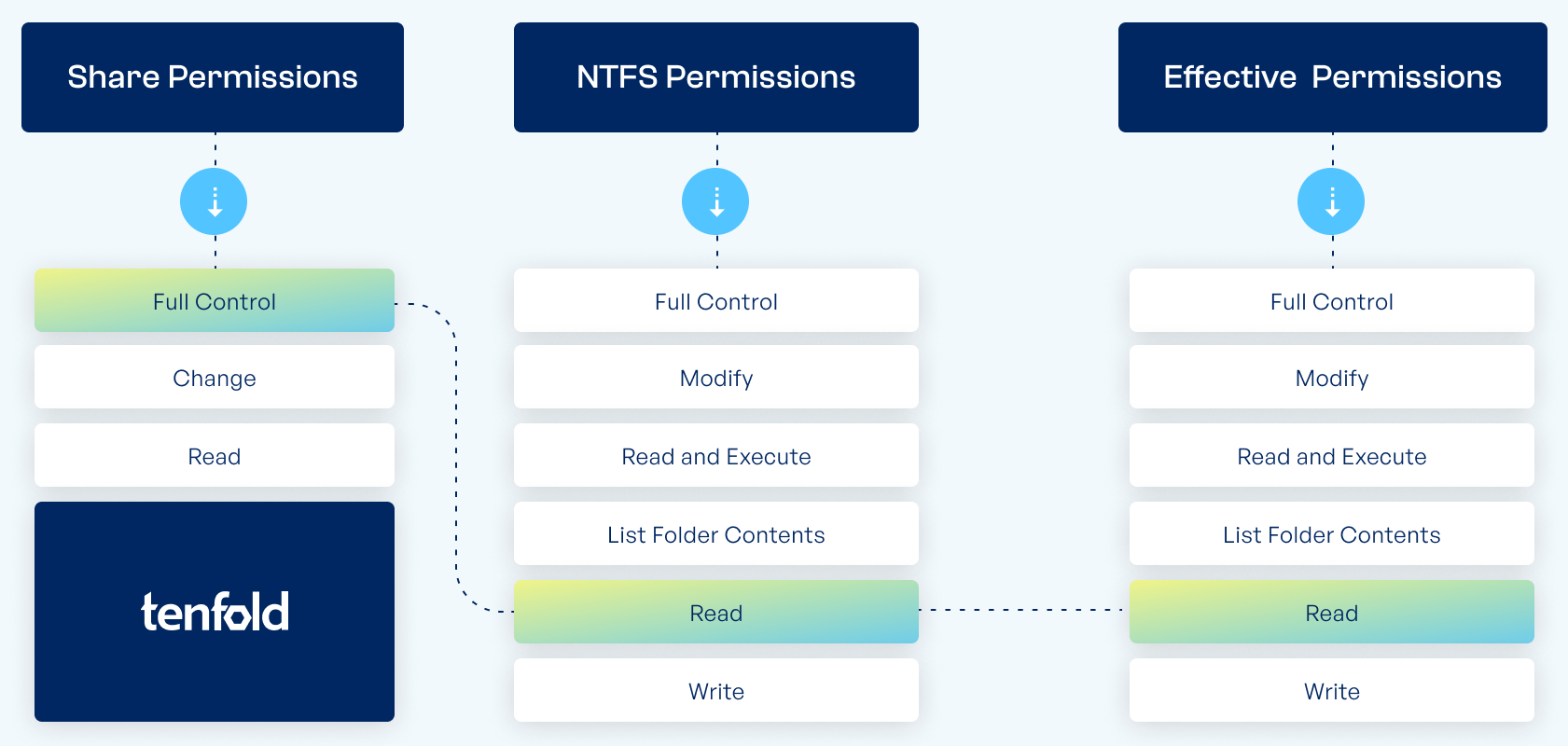
Differences Between NTFS and Share Permissions
| Share Permissions | NTFS Permissions |
|---|---|
| 3 permission levels (Read, Change, Full Control) | 6 permission levels (Write, Read, List Folder Contents, Read & Execute, Modify, Full Control) |
| Apply to network access | Apply to local and network access |
| Apply to the entire share | Can be changed for subfolders & files |
| Can limit concurrent access | Cannot restrict concurrent connections |
What Are Share Permissions?
Share permissions are used to control access to shared folders (and their subfolders and files) when accessed over a network. This means if access is made locally using a PC, the share permission has no effect. To set share permissions, right-click on the folder, go to Properties, click on the Sharing tab, then Advanced Sharing and, finally, click on Permissions. Unlike NTFS permissions, share permission levels are limited to “Read”, “Modify” and “Full access”.
Full Control: The user can change folders and files within the share, as well as edit permissions and take control of files.
Change: Users are permitted to read, execute, write and delete folders and files in the share.
Read: Users are permitted to view folder contents.
The Issue With Share Permissions
As a business, you want your identity & access governance to be as clear and straightforward as possible. But if you decide to rely on share permissions only, things are quickly going to get messy. The problem is that nested shares – where a folder is shared directly but also through one of its parent folders – can lead to users having different permission depending on the folder path they navigated through (direct vs. parent directories).
Access Governance Best Practices for Microsoft Environments
Everything you need to know about implementing access control best practices in Active Directory, from implementation tips to common mistakes.
Can You Combine NTFS and Share Permissions?
The short answer is: Yes, you can mix share permissions and NTFS permissions. But in order to do so, you need to understand which permission takes priority over the other. Else you might end up giving your employees too many or not enough rights.
When accessing a folder or file via network, both share permissions and NTFS permissions. If access is made locally on the file server, only NTFS permissions apply. The most important thing to remember, however, is that share permissions cannot grant a higher level of access than the active NTFS permission. It can only be used to further restrict the NTFS permission. Put more simply, the rule for combining NTFS and share permissions is as follows:
When share permissions and NTFS permissions are used together, the more restrictive permission takes priority.
Examples of Mixing Share and NTFS Permissions
Let’s examine how share and NTFS permissions behave when they are used together in the following example: Assume that access to our folder “\\srv\Department\Sales“ is made via network share and not locally (otherwise, share permissions wouldn’t even factor into it).
Example 1
If the sharing permission is set to “Read“ and the NTFS permission is set to “Full Control“, the user will only get “Read“ access to the file because the more restrictive share permission prohibits “Full control“ access via network.
Example 2
If the sharing permission is set to “Full Control“ and the NTFS permission is set to “Read“, the user will only have “Read“ access to the file. While the share permission would permit full access, the NTFS permission restricts access to “Read“.
Best Practices for Combining Share and NTFS Permissions
As you can tell, with only 3 permission levels, the security options for folder shares are very limited. Using NTFS permissions to manage access provides much more granular control, including the ability to set different permissions for subfolders. The main consideration for share permissions should be to make sure that they do not accidentally block access via the network because of conflicts with NTFS permissions.
We therefore recommend setting share permissions to “Full Control” for admins and “Change” for domain users. Do not set any other share permissions.
This way, it is guaranteed that the NTFS permissions you set take effect and will not be restricted when access is made via network. Using NTFS to control access on file servers brings the following advantages:
Combining NTFS permissions and share permissions is confusing and complex.
NTFS permissions offer more fine-grained control.
NTFS permissions apply even if access is made locally on the server.
Automated NTFS and Share Permission Management
Keep in mind that setting NTFS permissions comes with a few obstacles and considerations of its own. For example, there’s the issue of creating the necessary permission groups in the Active Directory to implement the AGDLP principle, Microsoft’s recommended group structure for Active Directory permission management.
Additionally, you may want to enable access-based enumeration in order to hide folders from users who do not have permission to view their contents. This makes it easier to navigate the file server, while preventing them getting the wrong idea from directories with telling names such as “2023_Restructuring” or “NY_Office_Staff_Changes”.
For organizations managing large groups of users, the easiest way to ensure safe and appropriate access accross your entire staff and IT landscape is to automate user and permission management through an IAM solution. Automated platforms for identity and access management assign and remove permissions based on the roles and access profiles you define (an approach also known as role-based access control), all while implementing best practices for Active Directory security and group structures. And the best part? tenfold saves time and frees up your admins to focus on more important tasks.
What makes tenfold the leading IAM solution for mid-market organizations?