Secure Password Transmission With tenfold
When you create a new user account in Active Directory, SAP or any other system, you have to set an initial password for the account. If you’re using tenfold to cover this process, the software generates a random password that complies with the password policies of the system you are creating the account for. The user then has to change the generated password the first time he or she logs on.
This is a very common procedure that has to be completed each time you create a new user. But how is the initial password communicated to the user? That’s something you need to think about. There are a number of methods to pass on credentials to users and we’re going to explore what they are.
Method 1 – Email
Yikes. Sending someone their user name and password within the same email is really the worst possible choice you could make. This method bears many risks:
Sniffing. This is when emails (containing credentials, for instance) are illegally intercepted using a sniffer application.
Hacking. A classic, easy way for attackers (who know what they’re doing) to obtain passwords and get immediate access to sensitive data.
Accidental forwarding of emails. Yep, it happens, and if it does, passwords may fall into the wrong hands.
Method 2 –Two Emails
The method of splitting credential information in two, i.e. one email containing the user name and one containing the password, is hardly better than Method 1. The only difference is that it won’t have quite the same dramatic effect if you accidentally forward one of the emails. The other risks – sniffing, hacking – remain the same.
Transmitting Passwords via One-Time Secrets
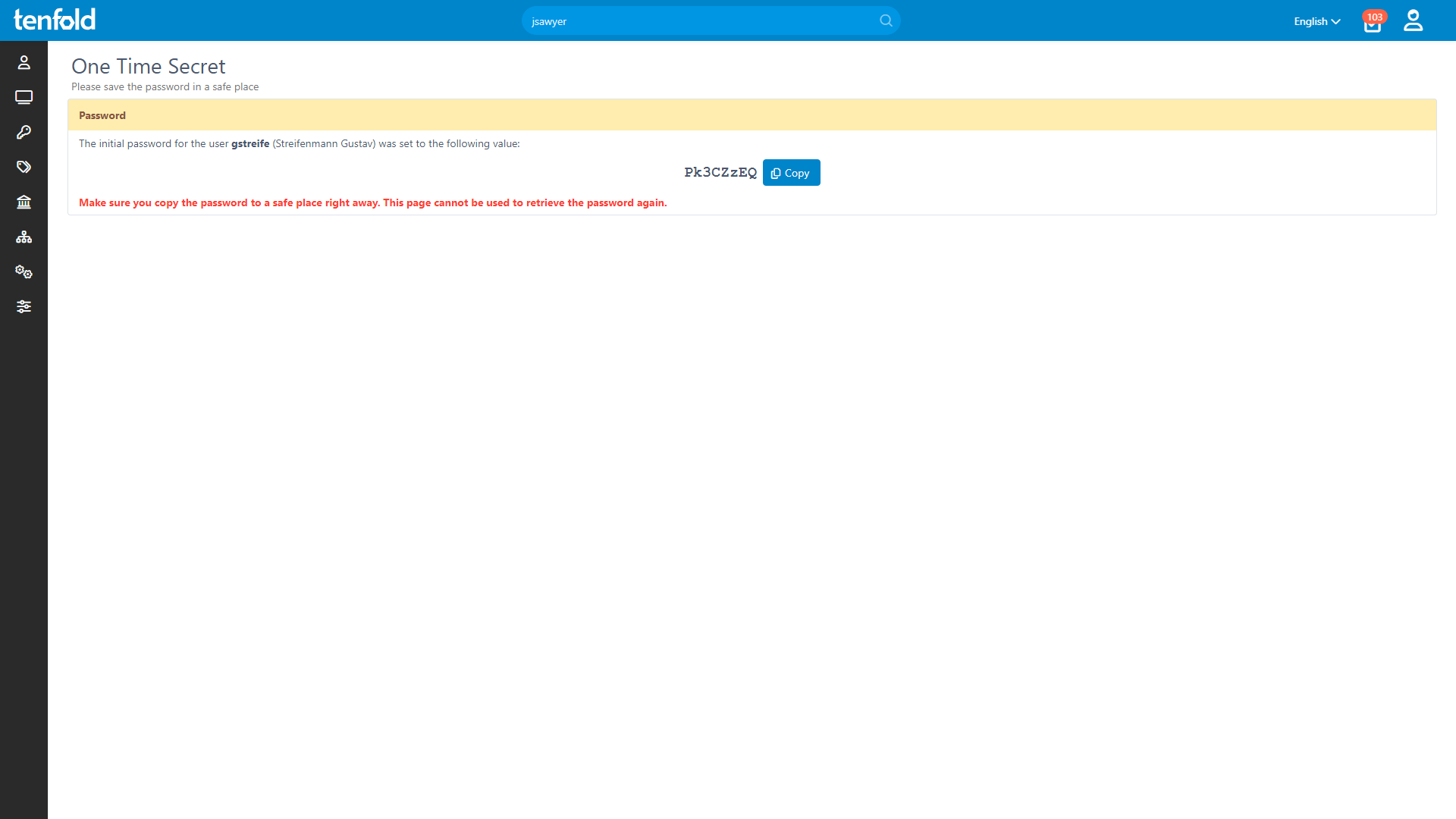
tenfold uses a mechanism called One-Time Secrets (OTS) for generating and transmitting initial passwords. Here, too, the user receives an email.
The difference is that the password is not shown in plain text in this email. Instead, the message contains a unique link that leads to a secure website.
The recipient must authenticate himself to tenfold via the link. The authentication is done using either single sign-on (SSO) via Kerberos or multi-factor authentication (MFA). The linked page opens only if the authentication was successful and the user is identified as the legitimate recipient of the password.
tenfold displays the initial password one time in plain text. The user can either use the password to log on or choose to pass it on in a secure manner. As soon as the link has been used once it becomes invalid and cannot be reused. If the link is not used within 7 days, it expires automatically and the password can no longer be retrieved.
Secure Password Transmission With tenfold
The one-time secret mechanism employed by tenfold protects against both accidental and deliberate misuse of initial login credentials:
Attackers can sniff all they want, but intercepting network traffic will be of no use to them as passwords are never shown in plain text.
Only the actual recipient can read the password. Accidental forwarding of emails or misuse are ruled out.
The recipient is authenticated using a secure method (Kerberos and/or MFA).
Old, unused initial passwords cannot be extracted or misused.
OTS is currently supported in the Active Directory User Lifecycle and SAP ERP plugins.
Watch Our Demo Video to See tenfold in Action!