Survey: How IT Decision Makers See Identity and Access Management
On behalf of tenfold software, the market research company YouGov asked 400 IT decision makers about the use of identity and access management solutions in their company. Read on to learn more about the role identity and access management plays in the workplace and which challenges organizations with and without IAM software face in their day-to-day operations.
Why Do Businesses Need Identity and Access Management?
59 percent of all participants in the survey said that their organization already uses an identity and access management solution. Among this group, respondents named a number of different reasons for why they decided to implement an IAM system:
74% – Improving Efficiency in the IT Department
53% – Safeguarding Sensitive Data
47% – Meeting Compliance Requirements
38% – Reducing Costs
31% – Increased Transparency for IT Permissions
Although increased efficiency was the most common reason for implementing an identity and access management solution, participants also see the security benefits of a least privilege approach to IT permissions: 94 percent of the respondents who use an IAM solution consider it important to very important for data protection.
What Are the Challenges of Identity and Access Management Solutions?
Despite the many benefits of an IAM solution, implementing and operating the platform comes with a number of challenges. The most common problems identfied by participants were a lack of IT staff, lengthy setups, the high complexity and necessary programming knowledge of most systems, as well as difficulties connecting other applications used in their IT environment.
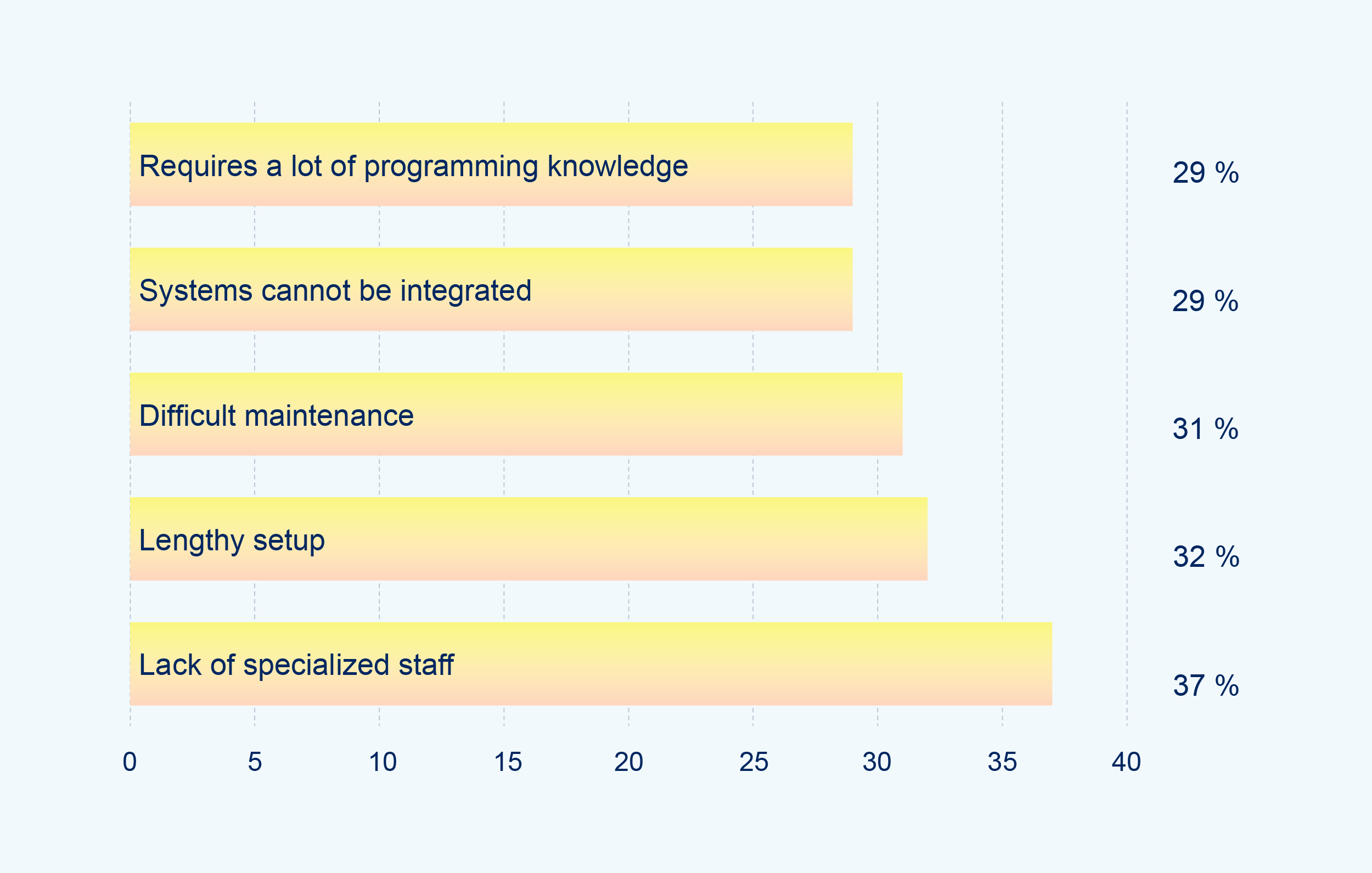
In other words: The biggest criticisms companies companies have when it comes to IAM software are the exact issues tenfold solves through its quick implementation and easy-to-use platform. tenfold offers a library of standardized plugins that can be configured quickly and easily through visual interfaces alone – no need for scripting or custom code! This allows you to set up tenfold quickly and with minimal effort: With tenfold, you’re ready to go in just a few weeks!
Risks Without Identity and Access Management
Among organizations who do not currently use an identity and access management solution (29 percent of participants), respondents gave a number of different reasons: 13 percent considered the topic too complex, 22 percent named a lack of budget as the limiting factor and 53 percent say they do not need an IAM solution. Overall, 43% of business plan to implement an IAM solution in the near future, 57% have no plans or gave no response.
Despite mixed interest, the importance of centralized user and permission management can be seen in the data concerning problematic access: Only 6% of the participants are certain that no one in their organization can access sensitive data they do not need. 42% estimate that less than a quarter of their staff can access resources they do not need, 24% assume a number higher than a quarter and 28% simply don’t know.
The confidentiality of business data is further threatened by the increased use of cloud apps like Teams and OneDrive: When it comes to file sharing in Microsoft 365, 51% of respondents see a medium to high risk of sensitive files ending up in the wrong hands. Only 9% see no risk of unwanted access through these services.
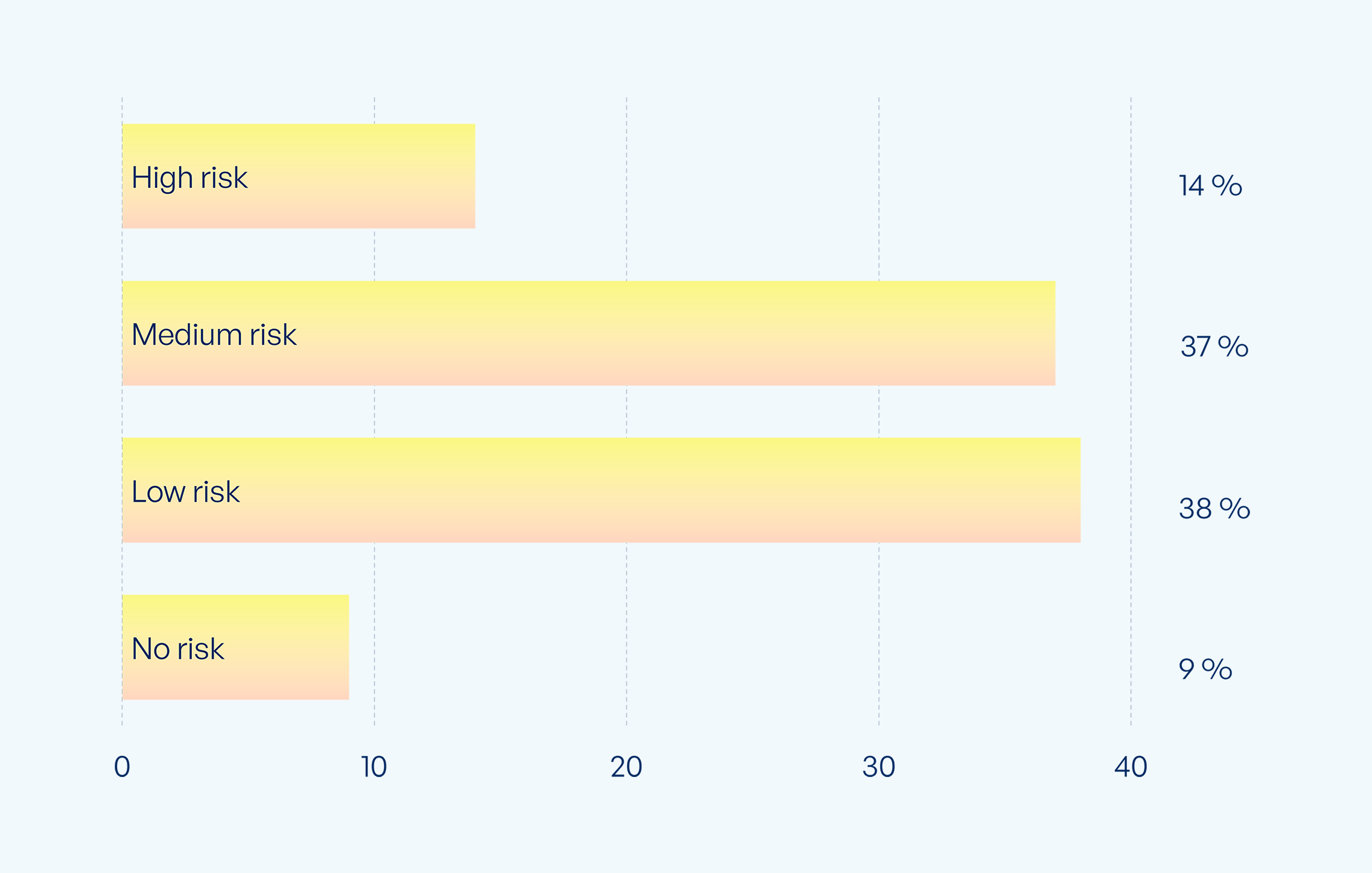
While the ability to share files with coworkers and external partners boosts productivity and communication, the liberal use of Microsoft 365 often leads companies to lose track of who exactly has access the which documents. This is especially concerning since the Microsoft Cloud offers no suitable tools to keep track of shared files or guest access.
This is another area where tenfold offers a simple and effective solution: By providing a central overview of shared files across Teams, OneDrive and SharePoint, tenfold makes it easy to review access and helps you keep both internal and external file sharing under control.
About the Study
The data shown here is based on an online survey by YouGov Germany that took place between May 25 and June 5 2023 and queried a total of 400 IT decision makers in organizations with more than 100 employees.