Our New, Free IGA Solution: Say Hello to the tenfold Community Edition!
Our new Community Edition makes it easy to take your first steps in professional Identity Governance & Administration. It’s the perfect tool for small to mid-sized businesses looking to streamline their user and access governance.
Free for up to 150 users – with full functionality and all plugins included.
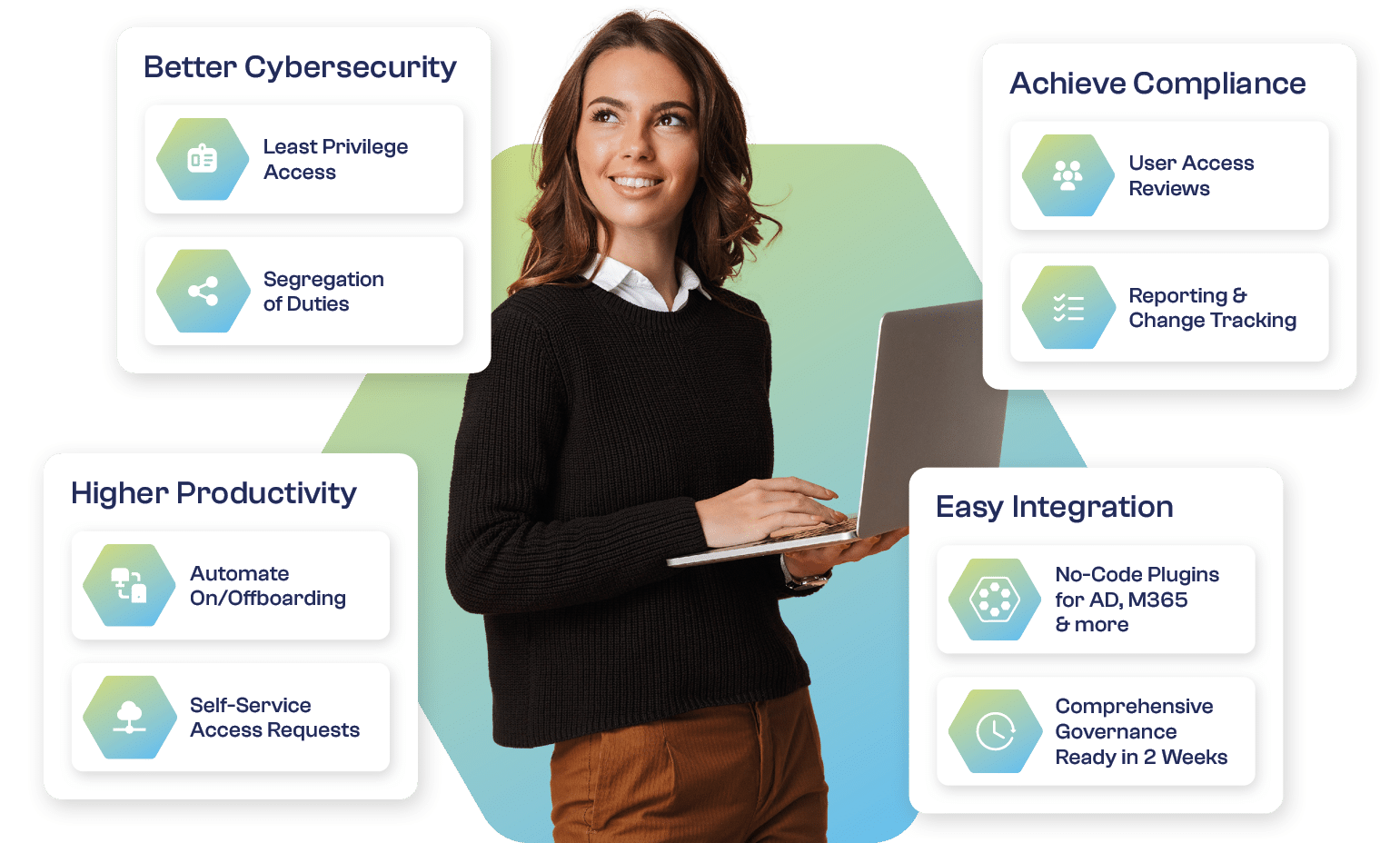
Governance Simplified
Delivering the right access to the right people at the right time.
tenfold empowers you to streamline operations, reduce risk and ensure compliance across your organization.
Enable Access
Seamless user onboarding in seconds
Empower teams with user self-service
Automate frequent governance tasks
Limit Privileges
Enforce role-based access control
Dynamically update roles & user access
Automate deprovisioning to reduce risk
Mitigate Risk
Achieve full visibility & central reporting
Automate audits & access attestation
Monitor guest access and shared files
Trusted by over 2,000 organizations worldwide
Complete Visibility
Gain full insight into access rights – from individual files to system-level oversight.
Centralized Governance
Govern access in Active Directory, Microsoft 365 and beyond through a single platform.
Fast Implementation
Achieve complete integration faster with our no-code platform and off-the-shelf plugins.
See how it works
With full visibility, central auditing and lifecycle automation, tenfold helps you regain control of IT privileges.
Watch our video overview to see it in action.
%
75
Lower IT Workload
%
95
Faster Access Provisioning
%
100
Privilege Creep Reduction
Experts love tenfold
The IAM experts at KuppingerCole Analysts praise tenfold as an efficient, mature & feature-rich solution. tenfold’s easy setup and operation make it the ideal choice for organizations that want to quickly secure their IT access.
Read the full review!
Learn more about tenfold:
Best Practice Guide
IGA Comparison
FAQ
Identity Governance & Administration (IGA) is a discipline of cybersecurity that ensures the right people have access to the right resources. It covers essential tasks such as user lifecycle management, access request management, centralized permission reporting and regular access reviews.
IGA ensures seamless access for all users while protecting critical data. By identifying and mitigating access risks, IGA allows organizations to prevent data breaches, boost operational efficiency and ensure IT compliance.
With hundreds of users and dozens of IT systems to manage, the need for access control has long outgrown the capacity for manual administration. If you want to mitigate access risks, prevent data breaches and ensure regulatory compliance, effective governance requires automation.
The good news is: IGA solutions do a lot more than just protect your data. Lifecycle management boosts productivity across the board by ensuring your users can access the resources they need – while saving your IT staff valuable time. And with self-service requests and password resets, IGA eliminates more than half of all helpdesk tickets.
Only tenfold offers comprehensive Identity Governance & Administration through an intuitive, no-code platform – IGA has never been easier.
Conventional IGA solutions require custom scripts to integrate with your IT. Building these interfaces and workflows takes a lot of time and effort, which complicates both initial setup and any later changes.
By contrast, tenfold provides ready-to-use plugins that make it easy to integrate Windows, cloud and business applications, all without writing a single line of code! Thanks to this revolutionary approach, tenfold allows you to automate your access governance in just a few weeks.
tenfold is a governance solution that helps you automate common IGA tasks like account provisioning, lifecycle management, access reviews and permission reporting.
However, tenfold is not a single sign-on (SSO) platform and will not help users sign into other apps connected to tenfold. We are also not an MFA provider, meaning tenfold cannot be used to add multi-factor authentication to apps that do not already support it.
Of course, when it comes to signing in to tenfold itself, we do offer MFA through authenticator apps as well as SSO through Kerberos (Active Directory) or OAuth (Entra ID).
Finding the right IGA solution is a question of scale: Huge corporations need complex frameworks that enable them to build their own fully customized platform – even if it takes years to do so. For most organizations, however, a simple and easy-to-use solution is the better choice.
tenfold fills this role perfectly by combining comprehensive governance with quick and easy deployment thanks to our built-in plugins and no-code interface. Don’t waste time on endless setups! Stop data breaches, eliminate access risks and maximize your IT productivity with tenfold – the IGA solution that works without the wait.
tenfold is available in three different editions: Essentials, Essentials 365 and Enterprise. All three editions give you access to our full range of features, including lifecycle automation, self-service workflows for access requests and password resets, central permission reporting and regular access reviews. However, higher tiers allow you to manage additional systems through tenfold.
tenfold Essentials allows you to manage on-premise systems such as Active Directory and file servers. Essentials 365 expands coverage to include Microsoft Cloud apps such as Entra ID, Teams, SharePoint and OneDrive. tenfold Enterprise additionally includes plugins for third-party applications like SAP ERP, HCL Notes or help desk platforms.
tenfold runs on-premise and is not a SaaS solution. In order to deploy tenfold, organizations need to provide a Windows Server Standard and Microsoft SQL Server or Oracle Database database. Our team of expert consultants will help you install and configure tenfold, providing you with a fully automated governance platform in as little as two weeks.
If you’d like to test tenfold in your own environment before buying, we offer a free 30 day trial that includes setup assistance and unlimited access to our tech support.
If you’re interested in purchasing tenfold, please contact our Sales team to help you choose the right edition and clear up any technical questions you may have. For pricing information, you can use our form to request a personalized quote and get a better idea of the costs.
You can always reach us at info@tenfold-security.com for general inquiries or sales@tenfold-security.com for sales-related questions.
Ready for the next step?
See tenfold in Action With Our Feature Video
Schedule a Live Demo With One of Our Experts
Put tenfold to the Test With Our Free Trial!